Security experts have recently found a database with an unheard-of 26 billion leaked data records. Known as the supermassive data leak or ‘mother of all breaches’ (MOAB), it’s possibly the biggest data leak ever discovered.
This huge leak includes data from many previous breaches and is about 12 terabytes large, which means it contains about 26 billion records. It brings together records from thousands of previous leaks, breaches, and databases that were privately sold.
This leak might be the largest one ever seen.
Bob Dyachenko, a cybersecurity researcher and the owner of SecurityDiscovery.com, worked with the Cybernews team to find billions of these exposed records. They found them in a database whose owner is likely to remain unknown.
The researchers think that the person owning this database might be collecting this data for harmful purposes. This owner could be a malicious entity, a person who trades in data, or a service that deals with lots of data.
Detailed Breakdown of the MOAB
The massive MOAB leak seems to include not just recent stolen data but is probably the biggest collection of data from multiple breaches ever seen.
Of the 26 billion records found, some might be repeats. However, the data is not just login details; it includes lots of sensitive information, which is very valuable to malicious parties.
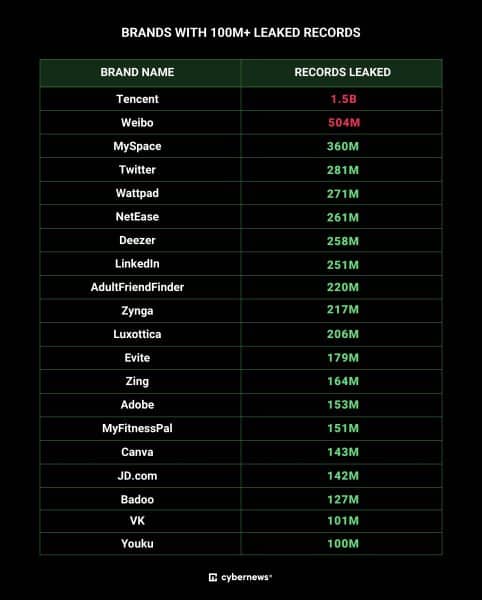
The largest chunk, 1.4 billion records, originated from Tencent QQ, a Chinese instant messaging app.
Additionally, the leak reportedly includes hundreds of millions of records from various platforms, such as:
- Weibo (504M)
- MySpace (360M)
- Twitter (281M)
- Deezer (258M)
- LinkedIn (251M)
- AdultFriendFinder (220M)
- Adobe (153M)
- Canva (143M)
- VK (101M)
- Daily Motion (86M)
- Dropbox (69M)
- Telegram (41M)
and numerous other companies and organizations.
It even includes records from government organizations in countries like the USA, Brazil, Germany, the Philippines, Turkey, and more.
The size of this leak is unprecedented. To put it in perspective, a huge leak in 2021 reported by Cybernews had 3.2 billion records – that’s only 12% of what the MOAB of 2024 contains.
How to Check if You’re Affected & How Protect Your Security
Using the Cybernews data leak checker, you can check if your information was affected in past breaches. The team is working on updating this tool to also include data from the MOAB leak. Another option is the free Have I Been Pwned service.
If you find out your data was involved in the recent massive data leak, it’s important to act quickly to protect yourself:
- Change Your Passwords: First, update your passwords for all online accounts, focusing on those involved in the leak. Make sure each password is strong and different from the others to avoid risks.
- Enable Two-Factor Authentication (2FA): Turn on 2FA wherever you can. It adds a second check to make sure it’s really you logging in, even if someone else knows your password.
- Watch Your Accounts: Keep an eye on your bank and other personal accounts for anything odd. Early detection of suspicious actions can prevent further damage.
- Stay Alert to Phishing: Watch out for suspicious emails or messages. Hackers use leaked data to trick you into clicking harmful links or downloading bad attachments. Don’t click anything from someone you don’t trust.
- Update Security Questions: If you use security questions to get back into your accounts, change them, especially if the leak might have included your answers.
- Check Your Credit Reports: Regularly look at your credit reports for signs of identity theft and report anything you don’t recognize.
- Use a Password Manager: Think about using a secure password manager to help you keep track of all your different passwords.
- Protect Your Documents: Make sure your important files are encrypted, and think about using safe cloud storage for them.
- Legal Action: In cases of significant loss or damage, explore legal options. Some jurisdictions offer protection and recourse for victims of data breaches.
Following these steps can help lower the risk from data breaches and safeguard your online identity. Remember, proactive measures are always better than reactive ones in the realm of cybersecurity.