In today’s digital era, where computerized systems are the norm, being aware of cybersecurity trends is crucial for safeguarding data, business assets, and customer trust. As the threat landscape evolves, keeping up with the latest cybersecurity trends is the key to building resilience, maintaining a good reputation, and preventing financial losses.
Finding valuable insights can be challenging as trends are spread across various reports and sites. That’s why we’ve used our expertise at Business2Community to deliver 14 key cybersecurity trends for 2025 and beyond.
Key Cybersecurity Trends
- Damage from cyber attacks will amount to nearly $10.5 trillion by 2025.
- 83% of breaches involve external actors and 74% involve human error.
- In Q3 2023, phishing volumes increased by 173% while malware rates increased by 110%.
- Threat actors from China and Russia are behind 75% of new threats in 2023.
- Zero Trust Network Access (ZTNA) will grow by 31% in 2023 and replace VPNs by 2025.
What are 2025’s Cybersecurity Trends?
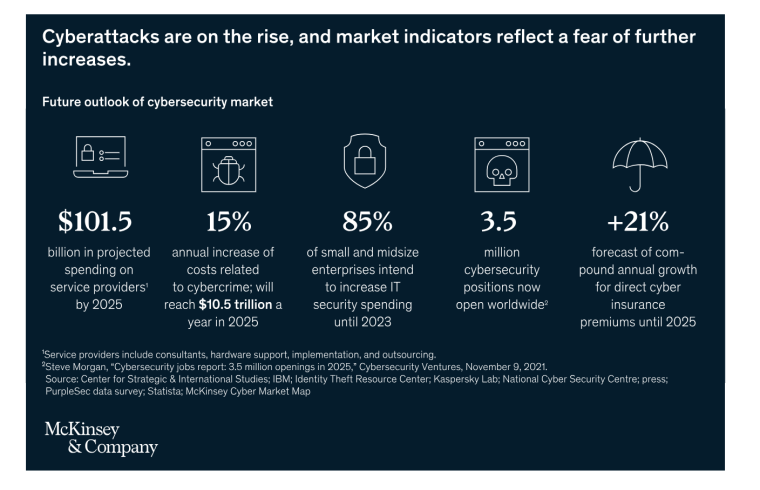
At the current rate of growth, cybercrime is expected to cost the world over $8 trillion in 2023. Damage from cyber attacks will amount to nearly $10.5 trillion by 2025 according to McKinsey, a whopping 300% increase from 2015 levels.
As costs mount, cyber security trends are the edge businesses need to strengthen their security solutions and stay ahead of threat actors. With that, let’s dive into the top cybersecurity trends in 2023.
1. Evolving Cybersecurity Landscape
Key developments in cybersecurity include:
- Microsoft’s 2022 block on macros has led to a rise in spam campaigns using container payloads like ISO, IMG, and VHDX for malware delivery.
- There has been a steady decline in large-scale botnets for the past 15 years. Major botnets such as TrickBot, Bazar, and Qakbot have been rendered inoperable.
- New versions of Emotnet, a malware-as-a-service featuring more advanced evasion-detection capabilities have emerged.
- Following recent successful law enforcement efforts, many groups have banned the targeting of critical infrastructure and government sectors to avoid scrutiny.
- As web browsers have more protections preventing pop-up abuse, attackers have shifted to using system browser notification features to force similar types of interactions.
- Talent shortages persist, with over 660,000 cybersecurity-related job openings in the US cybersecurity industry between May 2022 and April 2023, a 28% increase from the same time period in 2020.
2. Remote Working Cybersecurity Concerns
As remote workers are more likely to use personal devices to connect to employers’ secure networks, complex cyber threats have emerged. Among them are BEC scams and compromised credentials.
BEC Scams
Business email compromise (BEC) is a major financial threat to organizations.In 2022 alone, the IC3 recorded 21,832 complaints related to BEC, resulting in losses exceeding $2.7 billion.
Despite potentially lower individual losses, its prevalence is causing more total damage than ransomware. As of 2023, threat actors are turning to:
- The use of offline HTML login pages to circumvent detections that look for malicious executables or documents that auto-forward users to fake login pages.
- Using tactics such as social engineering to convince victims to approve an authentication request and bypass multi-factor authentication (MFA).
- MFA fatigue attacks which send many authorization requests in quick succession.
Info Stealers
Info stealers were linked to 31.5% of all malware detections and 32% of all ransomware incidents.
Due to the use of home and personal devices in remote work, there has been an increase in the use of info stealers. Some of the biggest marketplaces for info stealer logs have seen up to 2.5 times more logs advertised for sale (2.9 million to 7 million).
3. Social Engineering Attacks
Social engineering attacks are on the rise and to gain access to sensitive data, attackers are using tactics such as spear phishing and identity theft.
According to a 2023 Verizon report:
- 83% of breaches involve external actors, with the majority being financially motivated.
- 74% of breaches involve human error or misuse.
- 50% of all social engineering attacks are pretexting incidents, almost double the previous year’s total.
High-profile data breaches targeting casino giants MGM Resorts and Caesars Entertainment have highlighted the challenges companies face in defending against social-engineering attacks.
Hackers accessed Caesar’s networks after targeting one of its outsourced IT vendors with a social-engineering attack resulting in stolen data and losses of $100 million.MGM’s cyber attack which resulted in over $52 million losses also began with a LinkedIn-based social engineering scam.
4. Ransomware Attacks
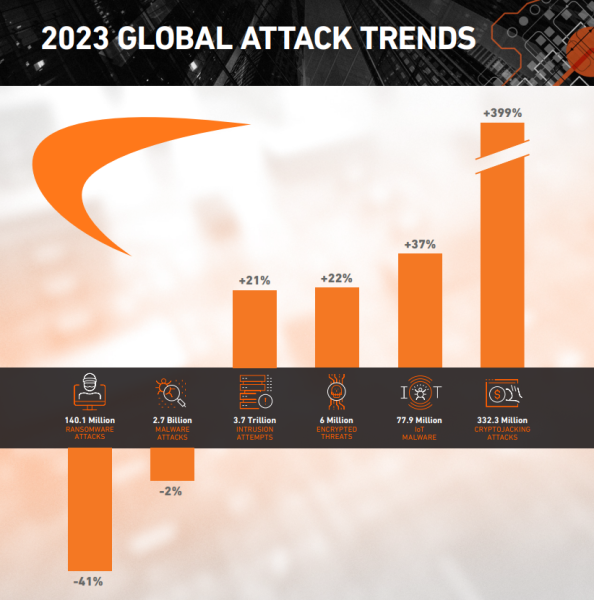
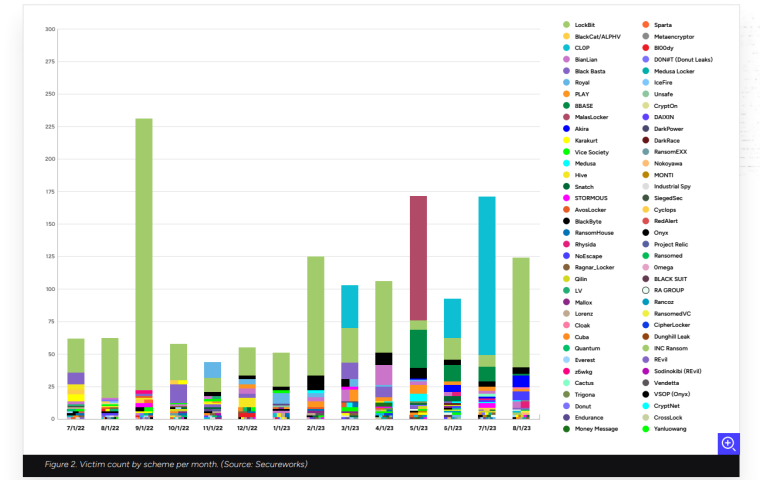
Ransomware incidents have now exceeded historical norms, making 2023 the most prolific year for ransomware attacks to date. However, devastating enterprise-wide encryption events, which are more difficult to execute and take longer to carry out, are now rarer.
Average dwell times have dropped significantly from 4.5 days in 2022 and 5.5 days in 2021 to just 24 hours in 2023. In a recent SecureWorks report, ransomware was even deployed within five hours of initial access in 10% of cases.
In Q2 2023, 34% of ransomware attacks in worldwide organizations resulted in a ransom payment,down from 45% in the previous quarter. However, the average amount of ransom paid more than doubled from nearly $328,000 in Q1 in 2023 to over $740,000 in Q2 of 2023.
Ransomware as a Service
Ransomware as a service or RaaS is on the rise. LockBit, often spread through phishing emails, remains one of the most pervasive RaaS variants today, accounting for 17% more ransomware incidents than any other strain.
5. Malware Attacks
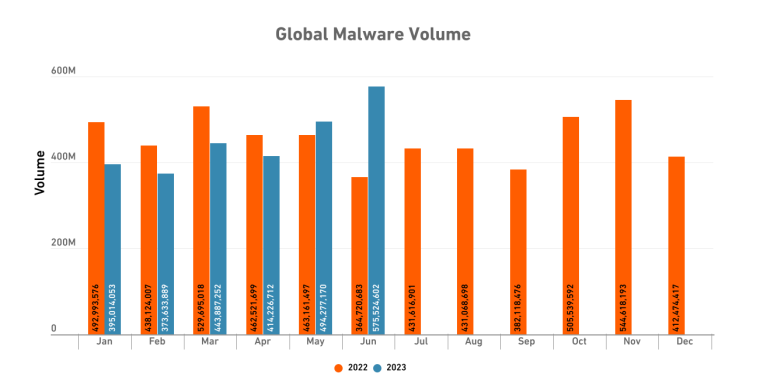
Malicious software, which is used to steal sensitive information has also seen a steep rise in 2023, increasing by 110% between Q2 and Q3. Malware volumes have set a record high, surpassing all Q3 totals since Vade began tracking incidents in 2015. Further:
- 35% of the malware attacks detected were either ad-click bots, crypto-miners, or banking trojans.
- Adware decreased by 25%, crypto-mining kept stable, and banking trojans almost doubled, climbing from 5% of malware attacks in 2021 to 9% in 2023.
- Residential malware infection rates continue to decline, falling from 3% to 1.5% but remain above the pre-pandemic rates of 1%.
Based on SonicWall’s threat data, cybercriminals are shifting their sights from North America to Europe, Latin America, and Asia. What’s more:
- EU governments and agencies have been targeted by spear phishing campaigns malware via malicious MS Office and PDF files.
- Politically motivated attacks have targeted journalists, government officials, and activists in Latin America.
- Several malware campaigns targeting Asian countries have been identified.
6. Phishing Attacks
Cybercriminals continue to exploit vulnerabilities in email, SMS, and voice communications to launch sophisticated phishing attacks. In Q3 2023, a Vade report detected that phishing volumes had increased by 173%.
Facebook and Microsoft remain favorites among hackers, with both being the first and second most impersonated brands since 2020. In Q3 2023, Facebook was the most impersonated brand and experienced a 169% increase in phishing URLs compared to Q1 and Q2 2023.
Meta Business Page owners are receiving scam messages, allegedly from the Meta Security Team, stating “Your Business Page Has Been Disabled” or “Violations detected may result in your Page being removed”. Similar Instagram copyright infringement scams are also on the rise. These social media-based phishing campaigns act as a back door, giving bad actors access to private digital data.
7. Crypto-Jacking
Cybercriminals continue to shift away from ransomware in favor of stealing computing power to mine digital currency. In the first six months of 2023, crypto-jacking attack volumes more than tripled, increasing by over 399% to more than 332 million hits. This marks a new record high exceeding even the full-year totals for 2020, 2021, and 2022 combined.
According to a SonicWall report, major crypto-jacking developments in the first half of 2023 included:
- Threat actors have accelerated their shift from targeting endpoints to targeting cloud services.
- MacOS devices are being targeted, with fake versions of FinalCutPro spreading HonkBox crypto-jacking malware.
- Oracle WebLogic servers are the target of a new crypter (a type of software that makes malware harder to detect) known as ScrubCrypt, designed to evade Windows Defender protections.
- Attackers are now skipping crypto-jacking altogether in favor of stealing crypto directly.
8. Cloud Security Concerns
Cloud security threats skyrocketed between 2021 and 2022. Cloud exploitation cases grew by 95% and cases involving cloud environments have nearly tripled, increasing by 288% year-over-year.
As per a 2023 Crowdstrike report:
- Nation-state and criminal adversaries are using cloud infrastructure to host phishing lure documents and malware.
- Threat actors are implementing command-and-control channels on top of existing cloud services.
- In 28% of incidents, adversaries manually deleted a cloud instance to remove evidence and evade detection.
- Human error and poor identity access management were identified as key cloud access points.
Research by IBM has shown that 82% of breaches involved data stored in the cloud, public, private, or multiple environments. Plus, 39% of these breaches now involve multiple environments and incur a higher-than-average cost of $4.75 million.
9. Attacks on IoT Devices
The Internet of Things (IoT), or the billions of physical devices that collect and share data via the internet, face rapidly expanding security risks. Forecasted to number 29 billion by 2030, these connected devices have seen a 400% increase in malware attacks in 2023.
According to a ZScaler report:
- 52% of IoT device traffic comes from manufacturing and retail companies.
- There are over 6,000 weekly attacks in manufacturing.
- IoT malware attacks in the education sector increased by nearly 1,000% in 2023.
10. State Sponsored Threat Actors
State-sponsored threat actors remain a threat to businesses worldwide. As per a 2023 WatchGuard Technologies report, threat actors from China and Russia are behind 75% of new threats in 2023. Additionally, 75% of new threats exposed this quarter hold strong ties to nation-states.
International state-sponsored attackers remain driven by political imperatives. In 2023:
- Russia’s key focus areas were the war in Ukraine, espionage, and cyber warfare.
- China’s key focus areas include cyber espionage as well as political and industrial secrets.
- North Korea’s key focus areas include cyber espionage and cryptocurrency theft.
- Iran’s key focus areas include monitoring dissidents, sabotage, and the suppression of opposition.
11. Mobile Threats
In 2022, 60% of the endpoints accessing enterprise assets were mobile devices. Employees now rely on mobile devices to interact with apps, conduct financial transactions, collaborate, and access data.
They are also a common additional factor in multi-factor authentication (MFA) solutions that govern access to corporate resources, including desktops and laptops. This cybersecurity trend is creating a larger attack surface, and an increasing number of bad actors are now exploiting this vulnerability.
According to a 2023 Zimperium report:
- 80% of phishing sites now either specifically target mobile devices or are built to function on both mobile devices and desktops.
- The average user is 6-10 times more likely to fall for an SMS phishing attack than an email-based one.
- About 20% of successful phishing emails come from mobile devices.
- 14% of mobile apps using cloud storage are vulnerable due to unsecured configurations.
12. Artificial Intelligence
Many organizations are turning to artificial intelligence (AI), machine learning (ML), and natural language processing (NLP) to bolster automated security systems, aid automatic threat detection, and enhance real-time data monitoring.
According to IBM, organizations that use security AI and automation capabilities on average:
- Have a 108-day shorter time to identify and contain a breach.
- Report $1.76 million lower data breach costs.
AI is already playing a crucial role in building automated security systems and its practical applications are only set to expand. Security tools driven by AI and machine learning will likely grow in sophistication and capability, giving businesses enhanced protection against evolving threats.
The level of interest that threat actors are showing in AI suggests that they may soon develop more complex cyber security threats.
To date, the most common types of attacks include:
- Phishing lures and Telegram bots
- Phishing emails
- Malicious sites impersonating ChatGPT via typosquatting domains
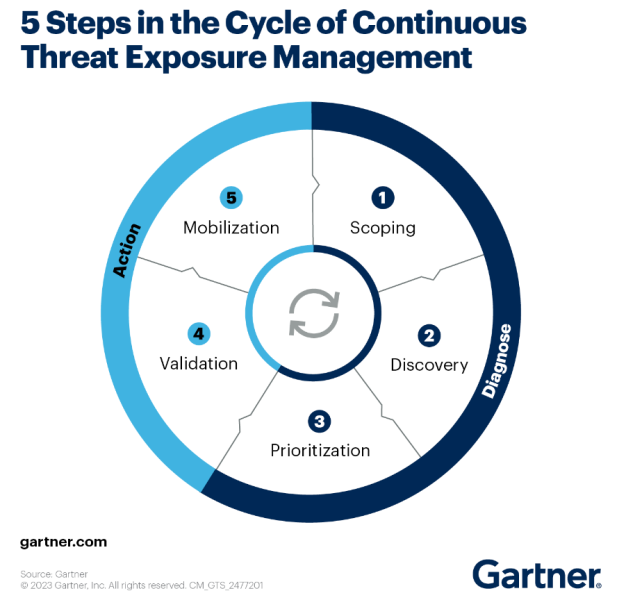
13. Threat Exposure Management
Today’s cyber attackers adapt quickly, often outpacing businesses’ efforts to enhance security and deploy security measures. As such continuous threat exposure management (CTEM) is essential to identify and prioritize the most pressing threats.
Gartner Research has identified CTEM as a priority that enables organizations to:
- Successfully manage a complex attack surface
- Reduce alert fatigue
- Improve cyber risk analysis and management
- Enhance their security infrastructure
- Improve data protection
By 2026, organizations and security teams that prioritize their security investments based on a continuous exposure management program will be 3x less likely to suffer a breach.
14. Zero Trust
According to a 2023 CyberEdge report, zero trust is expanding, driving investment in technologies like:
- Multi-factor authentication (MFA)
- Endpoint detection and response (EDR)
- Privileged account management (PAM)
80% of organizations are now using or implementing zero trust network access. Zero trust frameworks are becoming core organizing models for many security programs. When compared with organizations without zero-trust deployed, organizations with zero-trust deployed saved close to 20% in average breach costs.
Zero Trust Network Access (ZTNA), a rapidly expanding network security method, is projected to grow by 31% in 2023 and replace VPNs by 2025.
How to Find Cybersecurity Trends
Staying ahead of the curve in cybersecurity is absolutely vital for keeping your business’ systems and data safe. We shared some of the most important trends in the field right now but you should also know how to keep an eye on these trends on a regular basis. Let’s dive in.
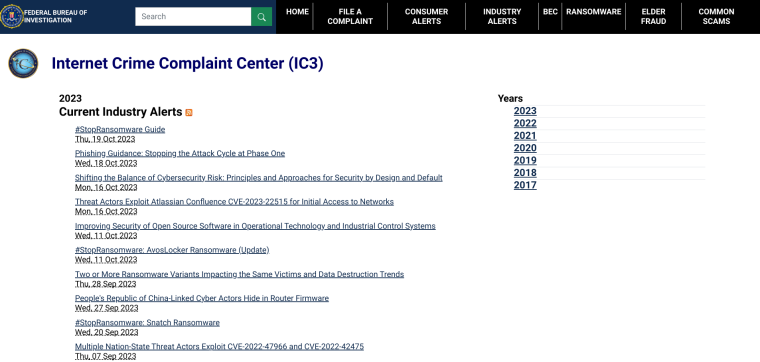
IC3 Industry Alerts
IC3 Industry Alerts are issued by the Internet Crime Complaint Center (IC3) and provide recent information on cyber threats like ransomware attacks, phishing attempts, and vulnerabilities exploited by bad actors. These alerts can serve as a valuable resource to find cyber security trends by offering current examples of threats and data breaches, and guidance on mitigating them.
Authority Sources
Authority sources from across the web are another great way to keep up with what’s happening in the cybersecurity space. Here’s how to find them:
- Read annual or quarterly cybersecurity reports from reputable cybersecurity organizations such as IBM, CISA, and IC3.
- Attend cyber security conferences.
- Join forums or online communities focused on cybersecurity.
- Read tech, data breach, and cybersecurity news from reputable outlets such as the Hacker News and Infosecurity Magazine.
- Follow blogs from cyber security firms or independent experts such as Graham Cluley and Brian Krebs.
- Subscribe and listen to podcasts that discuss online security trends such as SANS Internet Stormcenter Daily Cyber Security Podcast
The Future of Cybersecurity
Driven by the advent of technologies such as IoT, artificial intelligence, cloud-based services, and applications, the global cybersecurity market is anticipated to grow from $155.83 billion in 2022 to $376.32 billion in 2029.
In 2023 and beyond, a critical approach for counteracting human error, software vulnerabilities, and hardware issues in the cyber security space will be cyber resilience.
This holistic approach to cyber security is set to gain traction, giving global businesses the ability to navigate, recover from, and overcome an increasingly damaging threat landscape.