There has been a recurring thought concerning mobile phone security that has been on my mind lately, and as I have been discussing it with clients, it is beginning to make me nervous to know that others out there may not be as aware.
It started with this article I read that discusses the lack of support from mobile phone carriers for a “kill switch” for our smartphones in case they are stolen. Why? Cell phone thefts currently account for 30 to 40 percent of all robberies nationwide, and cost U.S. consumers more than $30 billion in 2012 according to data from the Federal Communications Commission. Wireless carriers are generating a substantial amount of revenue through their insurance programs offered for smartphones. If our phones had a “kill switch” (a means of completely disabling the phone), then there would be virtually no incentive for criminals to take them. As a result, if less phones are stolen it may mean less insurance sales for your mobile carrier.
While I don’t want to go into the corporate politics and other points being discussed in most articles, I do want to touch on the topic of the personal effects of losing your smartphone. In the past the most common fear of having your phone stolen – aside from the inconvenience of replacing it – was the potential access to personal items such as photos and text messages. Today there is much more to fear. Losing your smartphone may be worse than losing your wallet, and I believe it is important that everyone has an idea of what could happen if your unsecured smartphone falls into the wrong hands.
They Gain Access to Your World
At this moment at my desk I am signed into my Gmail, Twitter, and Facebook app, as well as several other applications on my smartphone. Apps such as these tend to remain logged-in by default because it allows users such as myself to access them faster.
The catch? If my phone was stolen I could still be logged in to these applications. That means whoever has my phone can now access my Gmail, Facebook, and Twitter, too.
Many apps containing personal data remain logged in
With access to my Gmail application the thief can view all of my email. There is nothing stopping them from going to the login page of other accounts I own and following the “I forgot my password” link to send a password reset email to my primary email account. To make matter worse, any two-step verification system may send a verification code to this same phone. Using this method a clever criminal can then reset the passwords to other accounts. Even your online banking account may be at risk. The Chase banking app, for example, may not keep you logged in, but it does keep your username available and advertises that the owner of the phone may likely have an online account with Chase. Having already gained access to your email, a simple attempt to reset the password using that username may be all that it takes to hijack your account. And yes – they could run the “forgot password” link for your iCloud account as well!
Have you ever sent yourself a copy of an important document to keep it for your records (such as a tax return) or backed up data to your Google Drive? Is Dropbox currently open on your smartphone? Any unauthorized hands on your phone may have access to that also.
All of this can take place within minutes, and well before you have an opportunity to lock your phone or take any proactive steps to disable your mobile device.
What Can We Do?
There are several responsible practices that I can suggest for securing your smartphone:
Be aware. Part of the reason I am writing this is to make others aware that this can happen. Perhaps that little extra bit of responsible paranoia may help someone avoid a situation where the above could take place.
Setup a security solution. There are several ways of adding more security to your smartphone, such as installing apps on the handset, using a management console on the IT side, or signing up for a cloud-based service. Keep in mind that the time between losing your phone and realizing it may be in the wrong hands is critical when it comes to mitigating any possible damage.
For Google Android, there are applications such as Android Lost. Android Lost adds remote find and wipe capability, and also lets you set a password and lock the SIM card slot. In a corporate setting, IT managers deploying Android devices can enable native remote wipe capability by installing Google Apps Device Policy.
For Apple iPhones, you can easily setup iCloud to locate and remotely erase your iPhone. If you lose your phone, you can find it either by installing the free Find My iPhone app or through your account on icloud.com. Either tool allows you to remotely lock your phone with a passcode (if you haven’t already), play a sound, or remotely wipe your phone.
For Microsoft Windows Phone 7 and 7.5, users can sign in at www.windowsphone.com on a PC to locate their phone with GPS, erase all the data, lock their phone and display a message, or change their password.
For RIM Blackberry users, Research In Motion offers BlackBerry Protect, a free app that lets you find, lock, or wipe your BlackBerry from a remote location.
Keep in mind that none of these solutions are fail-safe. If a thief has possession of your smartphone before the remote wipe occurs, they could disable the network connection and hack away. Also, if the battery dies or there is no signal to receive commands, then you may also be out of luck. Your best insurance, therefore, is to disable the handset as quickly as possible, the same way you would call your credit card company the moment you noticed a credit card was missing.
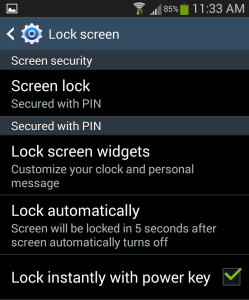
Enable a screen lock or password. A unique and simple password or PIN will provide a decent balance between security and ease of accessing your phone. No one wants to put in a long password after every time their screen goes dark, especially during those moments that you’re trying to snap a quick photo. I would suggest a 4-5 character PIN. Fingerprint and face recognition are generally regarded as less secure than a password or PIN.
Use a screen lock for additional peace of mind
Log out of applications. This may be the biggest pain, but also one of the best habits you can practice while we wait for a kill switch to be added to smartphones. The most popular apps like Gmail remain logged in unless you manually logout or specify otherwise in their settings. Logging out of these applications can ensure that not one else will have free access if they have your phone, and that they can’t use your email account to do malicious things such as sending themselves password reset links to your other accounts.
Use common sense! Be aware of your surrounding when you use your phone. We see countless people on their phones in public every day. I believe our smartphones may be more precious than our wallets, and yet how often do you walk around public places while blatantly shifting through your wallet? Or on the bus? Or at a bar? We’re out in public on our phones every day. Sometimes it comes down to statistics, and the numbers can be frightening.
As we wait for support of an integrated kill switch to be added to our phones, we can only do our best to practice the best habits to ensure the security of our personal information. I hope this post will help someone become more aware of the risks, and I’d like to hear what you have to say. Do you have a favorite security application you use or any other advice for readers? Share them in the comments!