The security of operating systems has always been a touchy subject, and with leaks sprouting front, back, and center, security and privacy issues have become even more controversial. Apple has repeatedly said that they have stringent security measures in place, although doubts have been raised about that.
In a recent report, iOS author and former hacker – add forensics expert to that – Jonathan Zdziarski claims that Apple may have “inadvertently” admitted to having created an iOS backdoor.

He shares his analysis in the document Identifying Back Doors, Attack Points, and Surveillance Mechanisms in iOS Devices. He says that based on his findings, Apple has created “several services and mechanisms” by which personal data can be extracted from iOS devices by unauthorized entities – including Apple and government agencies.
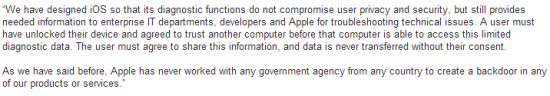
Apple has responded to this with a denial.
Zdziarski says, though, that this does not totally eliminate Apple creating an iOS backdoor. He bases this statement on the mention of “diagnostic functions” and “provides needed information to enterprise IT…”
In a blog post, Zdziarski states:
“…it looks like Apple might have inadvertently admitted that, in the classic sense of the word, they do indeed have back doors in iOS, however claim that the purpose is for “diagnostics” and “enterprise”. The problem with this is that these services dish out data (and bypass backup encryption) regardless of whether or not “Send Diagnostic Data to Apple” is turned on or off, and whether or not the device is managed by an enterprise policy of any kind. So if these services were intended for such purposes, you’d think they’d only work if the device was managed/supervised or if the user had enabled diagnostic mode. Unfortunately this isn’t the case and there is no way to disable these mechanisms.”
So who’s telling the truth? Do you think there is an iOS backdoor?