WhatsApp, a Facebook-owned company, is a mobile application that allows users to send text messages, voice calls, and share documents with other WhatsApp users. You may wonder why the app sounds familiar, it’s likely due to the Jeff Bezos attack in 2018 where his phone was hacked and the attacker stole GBs worth of personal data. This led to incriminating photos being released publicly of Bezos with his mistress, a very public divorce, and a roast at the Oscars by Chris Rock, all because of a cyber-attack involving WhatsApp. WhatsApp has been working to improve its security-related reputation ever since the 2018 Bezos attack.
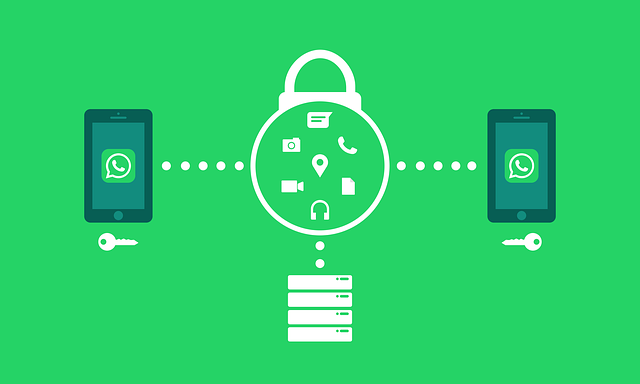
On September 10th, 2021, WhatsApp announced it will roll out support for end-to-end encrypted chat backups on the cloud for Android and iOS users, paving the way for storing information such as chat messages and photos in Apple iCloud or Google Drive in a cryptographically secure manner. When implemented properly, end-to-end encryption can prevent WhatsApp employees from snooping on its users. Normally, this wouldn’t be an issue, but when a subpoena is issued to What’s App they must comply if they’re able. End-to-end encryption prevents even WhatsApp employees from being able to capture and turn over these chat message histories to the authorities.
Previous Security Feature
Back in 2016, WhatsApp enabled End-to-End Encryption (E2EE) for personal messages, calls, video chats, and media between senders and recipients. The problem with this E2EE solution relates to users’ backup data in the cloud. When transferring conversations or data from user devices the same E2EE security protections were not possible, making backups readable by WhatsApp staff, government agencies with a subpoena, the cloud providers themselves, and even hackers inside cloud provider networks.
The New Feature
The optional feature will go live in September of 2021, but will only work on the primary devices tied to a users’ account; not companion devices such as desktops or laptops that simply mirror the content of WhatsApp on the phones. WhatsApp made a statement in a whitepaper:
“With the introduction of end-to-end encrypted backups, WhatsApp has created an HSM (Hardware Security Module) based Backup Key Vault to securely store per-user encryption keys for user backups in tamper-resistant storage, thus ensuring stronger security of users’ message history.”
With end-to-end encrypted backups enabled, before storing backups in the cloud, the application encrypts the chat messages and all messaging data (texts, photos, videos, etc.) using a random key generated on the user’s device. The device-generated key encrypting the backup is secured with a user-provided password, which is stored in the vault to allow easy recovery in the event the device gets stolen.
Alternatively, users have the option of providing a 64-digit encryption key instead of a password, but in this scenario, the encryption key will have to be stored manually given that it will no longer be sent to the HSM Backup Key Vault. When an account owner needs access to their backup, it can be done so with the help of the password or the 64-digit key, which, subsequently, is employed to retrieve the encryption key from the backup key vault and decrypt their backups.
The vault is geographically scattered across five data centers and is responsible for enforcing password verification as well as rendering the key inaccessible after a set number of unsuccessful login attempts; reducing the likelihood of brute force attacks.
What Should You Do Now?
If you’re a WhatsApp user, you should avoid using WhatsApp until this new feature is rolled out. Once the feature is released, CyberHoot recommends enabling this optional feature to reduce the likelihood of a data privacy breach.
Crucial Recommendations for SMBs from CyberHoot
While you’re waiting for the new What’s App E2EE security feature to be released, it’s vital you implement the following CyberHoot recommendations:
- Adopt a password manager for better personal/work password hygiene
- Require two-factor authentication on all SaaS solutions and critical accounts
- Require 14+ character Passwords in your Governance Policies and technology configurations
- Train employees to spot and avoid email-based phishing attacks
- Test that employees can spot and avoid phishing emails
- Backup data using the 3-2-1 method
- Incorporate the Principle of Least Privilege
- Perform a risk assessment every two to three years
- Hire a professional virtual Chief Information Security Officer (vCISO) to advise, guide, and build your cybersecurity program at a fraction of the cost of hiring an FTE.
Sources: