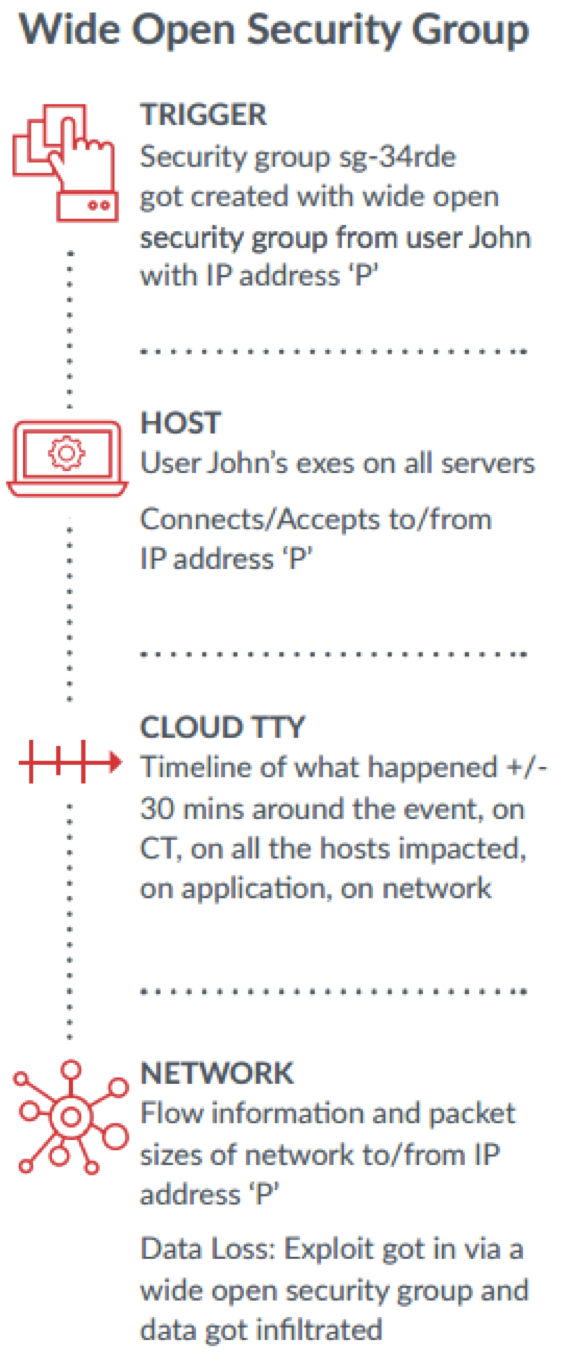
Some people go to great lengths to find things to disagree about, but I think there’s one thing all of us can agree on: cloud security keeps us on our toes. That’s because the cloud requires a fundamental change in the way we approach security challenges. As the scale and complexity of cloud environments increase, traditional tools and tactics become less and less effective, and security gaps widen. That is, if you don’t have a sound security strategy in place.
With so much FUD (fear, uncertainty, doubt) flying around, there is actually some good news about cloud security today: Considering that 93 percent of companies are now using cloud technology, IT professionals can finally shift their focus from cloud adoption to building a proper cloud security strategy around their cloud environments.
So if you’re on board with the idea that it’s time to develop a real cloud security strategy for your organization, we have a great template called SOSTAC® that you can leverage in your own strategy. Keep reading for a guided tour.
A Strategic Template for Today’s Security Needs
So what the heck is SOSTAC, you ask? Well, it’s a system that was developed in the ‘90s and originally used by companies to build and organize their marketing programs. However, we think its components provide a very useful way to map cloud security strategies too. To understand how, let’s start by breaking down the SOSTAC acronym:
- Situation – where are we now?
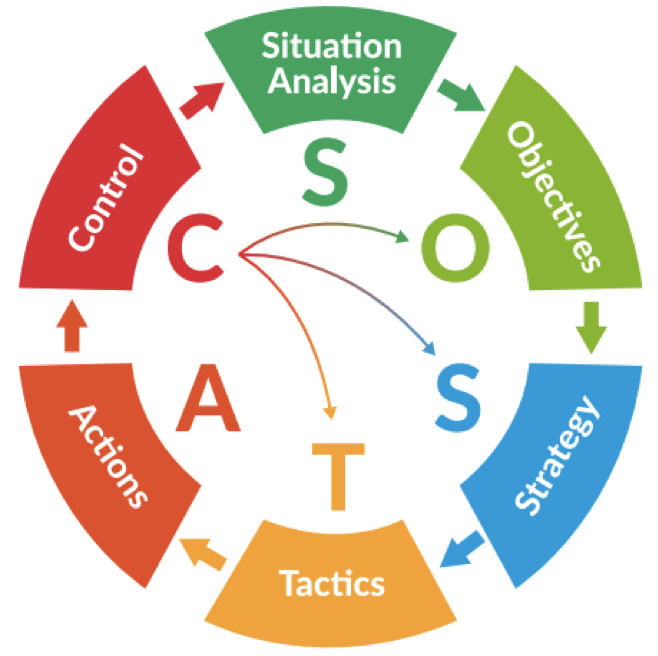
- Objectives – where do we want to be?
- Strategy – how do we get there?
- Tactics – how exactly do we get there?
- Action – what is our plan?
- Control – did we get there?
These are all really good questions to ask yourself as you set out to develop a comprehensive cloud security strategy. It’s important to identify not just where you want to end up but where you are now. After all, no one starts out with a completely blank slate.
Going a layer deeper, let’s examine how you can apply SOSTAC to today’s cloud security challenges.
1. Situation: Taking Inventory of Your Organization’s Security Practices
The first step is to examine your current cloud security posture. This is a good time to take an inventory of the security tools you are using, including everything from antivirus to firewalls to malware protection and beyond. If you have all of these and more, great. None of them? That’s okay too. That’s why you’re building out a strategy now. It will be easier to figure out what your future strategy needs to look like when you understand where you stand today.
Here are a few examples of what you should evaluate in order to determine your current cloud security posture:
- What processes do we have in place for security today?
- What must we absolutely protect above all else?
- What technologies are we currently using for security? Is there overlap or redundancy?
- What kinds of attacks are we most vulnerable to?
2. Objectives: Avoiding a “One-Size-Fits-All” Approach
Next, you need to determine your objectives. It’s important to note that objectives are not one-size-fits all, meaning that what works for one company may not work for yours, and vice versa. To determine the most effective objectives for your organization, you need to identify the biggest areas of concern for your industry, company, size, customer type, and business model. And it’s not enough to simply say you want to “secure the cloud”. You actually need to define specific objectives around the following eight functions:
- Workload Security
- Infrastructure Security
- Network Security
- Application Security
- Vulnerability Scanning
- Threat Intelligence
- Data Security
- Reporting
To get started, here are a few examples of good cloud security objectives:
- Meet HIPAA compliance
- Catch credit card fraud attempts
- Protect customers’ sensitive banking information
3. Strategy: Getting It On Paper For Accountability
Now, you need to put your strategy on paper, showing exactly how you’ll get from where you are now (Situation) to where you want to be (Objectives). Although it’s the least technical part of this process, the exercise of writing down your strategy is a good opportunity to make sure that all your stakeholders are on board with your plans and that they’ve all given their input before you get started.
Even more, having one document that all key stakeholders can reference when needed will ensure that you’re on the same page and that protocols are clear. And if things fall through the cracks, you’ll know why and whose responsibility it is.
4. Tactics: Implementing the Defense Line
In this step you lay out your tactics. For the purpose of security, this means building organizational processes and protocols, like alerting and baselining, that protect against specific vulnerabilities and types of attacks. Here’s an example use case:
In our popular (and free) Cloud Security Playbook, we demonstrate what the best practice cloud security tactics are and how to map them to the infamous Cyber Kill Chain, as well as exemplify what a complete defense looks like in action. As they say, the best offense is a good defense, so getting this part right is worth the read.
5. Action: Determining Your Detection and Response Capabilities
The cloud security software you choose will make a big difference in how well you’re able to execute on the strategy you develop, determining how effectively you’re able to detect problems and how quickly you can respond.
While the technology platform you select will ultimately depend on your goals, environment, threats, compliance regulations, and stakeholder requirements, you should be sure to cover the eight key functions (mentioned above in Objectives) in relation to the technology you choose. Not only does each of these categories solve for a critical area of security, but when implemented together, they make for a complete cloud security framework.
6. Control: Evaluating and Iterating
Remember that cloud security isn’t a “set it and forget it” proposition. For one thing, security threats evolve constantly, meaning that you need to continually adapt your security approach to stay ahead. Moreover, if you’re a high-growth company, it’s a good idea to reevaluate your risks and strategy periodically. To effectively meet your evolving security needs, we recommend that you test your strategy once it’s developed, and from there, schedule regular check-ins that can help determine whether you are meeting the goals you set.
After all, even the best intentions won’t do any good if you aren’t measuring real-world outcomes to see if your strategy actually works.
Putting It All Together
When you consider today’s volatile threat landscape, it’s clear we can’t keep operating by the seat of our pants. Developing a clear strategy will help you avoid the pitfalls of legacy approaches, save you time and resources in the long run, minimize the holes in your security process, and provide guidance as you grow and evolve. Using SOSTAC as a template enables you to build processes and invest in security platforms that support all your goals and protect your entire infrastructure.
Our Cloud Security Playbook details even more about each of these six areas of your cloud strategy, as well as real examples and printable worksheets to kickstart your own strategy creation.