Hackers get the headlines, but a data breach is more likely to originate inside your own office walls. Errors, negligence and malicious intent by employees are the leading causes of security incidents but remain the least reported.
Why do employees pose so much risk? The list of reasons is long: busy schedules that lead to sloppiness or oversights, the sheer volume of data handled in our digital world, lack of employee loyalty, apathy, use of personal and mobile devices for work, and more.
If you’re not yet concerned about insider threats, consider that:
- Sixty-two percent of respondents to a 2016 Ponemon Institute survey reported having access to company data they probably should not see. That’s up from just 38 percent in the same survey two years prior.
- In the same 2016 survey, 43 percent of businesses said it takes them a month or longer to detect employees accessing files or emails they’re not authorized to see.
- Only 9 percent of respondents to a 2015 SANS survey ranked their insider prevention methods as “very effective.” And nearly one-third of organizations said they have no capacity to prevent or deter insider incidents.
If you’d like to be on the rights side of statistics like these, there are steps you can take to significantly reduce the risk of a devastating data breach. The good news? These are steps you can start taking right away, even on a very limited small business budget.
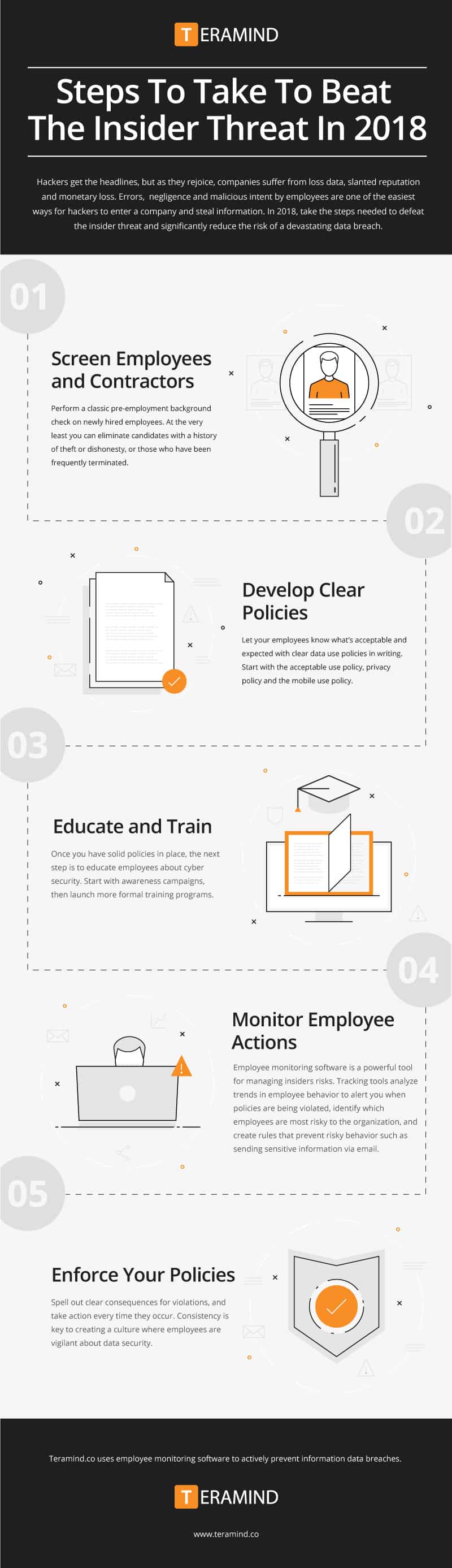
Screen Employees and Contractors
Any new hire presents a security risk, so it’s important to thoroughly vet potential employees before bringing them on board. Your classic pre-employment background check is a crucial step. It won’t tell you everything, but at the very least you can eliminate candidates with a history of theft or dishonesty or those who have been frequently terminated.
Personality tests can be a valuable tool as well. They’re not foolproof – some people can outsmart them by not being truthful – but you can eliminate anyone whose answers indicate dishonesty, an absence of loyalty, disorganization or apathy.
Develop Clear Policies
You can’t expect employees to know what’s acceptable and expected without clear data use policies in writing. In general, there are three policies you need:
- Acceptable use policy – How can company assets be used? Can business data be stored in the cloud or on USB devices? Which types of information can and cannot be shared by email?
- Privacy policy – What are employees allowed to do with company data? Will sensitive data be stored on the network? What safeguards are in place to protect sensitive data? How is employee data protected and encrypted?
- Mobile use policy – How is data accessed remotely, and what safeguards are in place for remote access? Can laptops be taken home? Can personal devices be used to access business data? If so, how must those devices be secured?
It’s wise to have a lawyer specializing in technology and data use either draft or review your policies, but you can also use online templates like this. Another great resource is the Federal Communications Commission’s Small Business Cyber Planner 2.0.
Educate and Train
Policies are useless if employees don’t know they exist. Once you have solid policies in place, the next step is to educate employees about cyber security.
Start with awareness campaigns, which focus attention on security by delivering information and tips through posters, email reminders or newsletters, rewards programs and brief learning sessions. Then launch more formal training programs that offer detailed information and provide employees with actionable steps.
Free and low-cost training materials are available online, but it can be difficult to weed through them to determine which are best. Check out this Better Business Bureau list of resources for cyber security awareness and education. ESET offers free Cyber Security Awareness Training, and the Center for Information Security Awareness offers affordable training modules on phishing and email scams, creating strong passwords, device management and more.
Monitor Employee Actions
Employee monitoring software is a powerful tool for managing insiders risks. Tracking tools analyze trends in employee behavior to alert you when policies are being violated, identify which employees are most risky to the organization, and create rules that prevent risky behavior such as sending sensitive information via email. The software records, logs and monitors all employee activity, allowing you to quickly identify the source if a breach does occur.
Enforce Your Policies
This almost goes without saying, but you’d be surprised how often companies create data use policies then fail to enforce them. Spell out clear consequences for violations, and take action every time they occur. Consistency is key to creating a culture where employees are vigilant about data security.
This piece originally appeared in IT Security Central and was reprinted with permission.