
The term “Internet of Things” (IoT) was introduced to the world by Kevin Ashton in 1999 as merely the title to a business presentation. Today, the term is used to describe a vast network of people and things — “smart devices” like cars, home control systems, wireless printers, gaming consoles, etc. — connected through the Internet.
A network of people and things
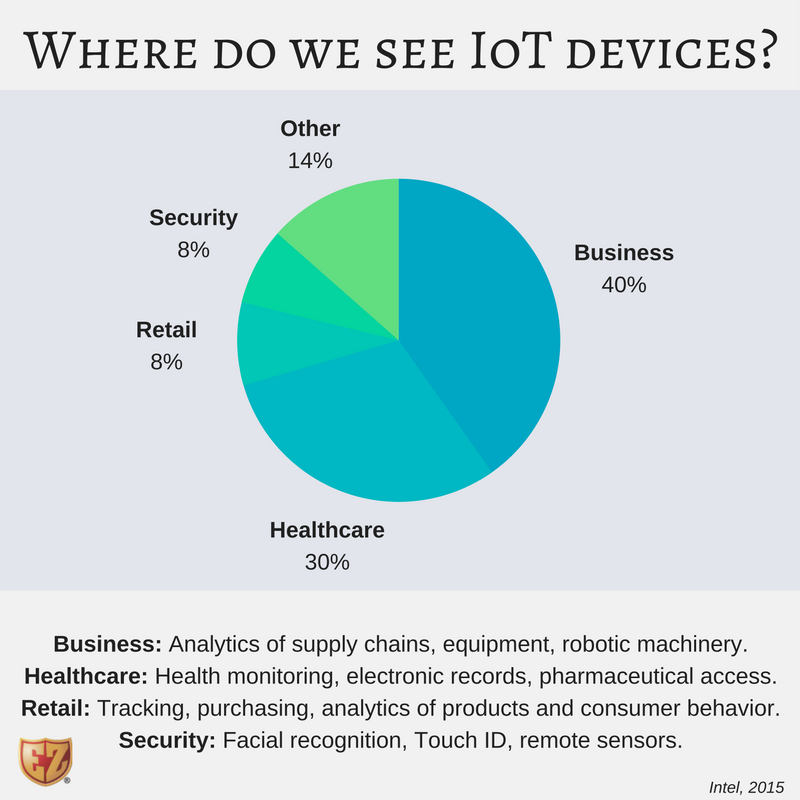
These small, affordable and easy-to-use devices allow both things and people to connect, and to transfer, store and share data. In short, the IoT market aims to advance technology in convenience, accessibility and efficiency for a consumer’s everyday life. These devices come in all shapes and sizes, ranging from a single chip that can monitor a person’s heart rate to full home systems that can control door locks and kitchen appliances.
An estimated 15 billion IoT devices were connected to the Internet in 2015, and that number will only continue to grow. By 2020, BI Intelligence predicts that there will be around 34 billion active IoT devices, and that IoT technology will become a $6 trillion market.
Ashton’s vision for IoT technology was to not only connect people, but to connect people and “things” simultaneously. Although computers and the Internet make using, exchanging and sharing data possible, Ashton argued that technology’s capabilities would mean nothing without “the most numerous and important routers of all: people.”
Convenience at the cost of security
The concept of IoT is still relatively new. Security experts note that this technology is growing faster than research can keep up with. Despite the innovative abilities that IoT brings to the table, the Federal Trade Commission (FTC) warns consumers that the technology’s independent nature can pose serious threats to personal information security.
IoT security concerns mostly focus on loss of privacy and unauthorized access to personal information. While the FTC recognizes that IoT devices offer ways to easily monitor, access and interact with data and people, the technology also creates new opportunities for criminals to commit identity crimes like identity theft and fraud. These devices are particularly targeted by hackers because they collect, transmit and share data over Wi-Fi networks. Once a network is hacked, criminals can gain access to other devices and any information stored on that network.
“Security risks in IoT can be exploited to harm consumers by: (1) enabling unauthorized access and misuse of personal information; (2) facilitating attacks on other systems; and (3) creating safety risks.”
— FTC 2016, The Benefits, Challenges, and Potential Roles for the Government in Fostering the Advancement of the Internet of Things
Why are IoT devices so vulnerable to cyberattacks? Much like computers and smartphones, IoT devices run on software that requires regular patches and updates. Simply put, consumers are not used to regularly updating devices like toasters, light bulbs or alarm systems as they do for computers, smartphones and other personal devices. As a result, software companies have also had difficulty approaching this issue, leaving consumers with limited available security measures to protect their devices.
Furthermore, the information sharing capabilities that come with these devices, paired with the ability to control these devices through third-party applications, can also leave users vulnerable to unauthorized access to their personal networks. A FTC study found that third-parties often collect data from IoT devices, which can include (but is not limited to) device identifiers, location data, demographic information and search histories.
What should you do?
As the IoT market continues to evolve, what can you do to protect your devices and yourself from compromise?
- Consider setting up a separate network for your IoT devices. By keeping IoT devices and other information separate, hackers will have a harder time gaining access to your sensitive information.
- Never connect your IoT devices to unsecured networks. Be sure to create strong passwords for your Wi-Fi networks. The easiest way for hackers to gain access to your home devices is to compromise your Wi-Fi network.
- Look into available security measures offered for your smart devices. If possible, be sure to continuously update your IoT software since these devices are especially susceptible to cyberattacks.
There is no need to ditch the many conveniences IoT devices provide. Just take the necessary precautions to avoid having your information compromised in the process.