A wave of phishing attacks has been generated within Google’s cloud-based word processing solution (Google Docs) and its “Comments” feature. Attackers use the commenting feature to send malicious links to anyone’s email inbox. What’s worse, the comment appears to come from anyone hackers want it to be. In other words, a hacker can send a malicious link to you from your best friend on social media, and nothing stops that email from landing in your inbox supposedly sent by your best friend. Hackers have hit 1000s of inboxes by exploiting this Google Doc’s feature according to online reports. This is a gold mine for hackers.
How Does It Work?
Hackers target Google Docs users by adding a comment to a document that mentions the targeted user with an “@,” which automatically sends an email to that person’s inbox. That email, which comes from Google, includes text as well as potentially malicious links. What makes this attack so dangerous, is that normally Google and Outlook filter out malicious links within an incoming email. However, in these “comments” based attacks, the phishing emails bypass email security checkpoints because they are coming from a trusted source, Google.
Side note: Security researchers reported the same outcome when attempting to exploit Google Slides, the suite’s presentation app.
The Emails
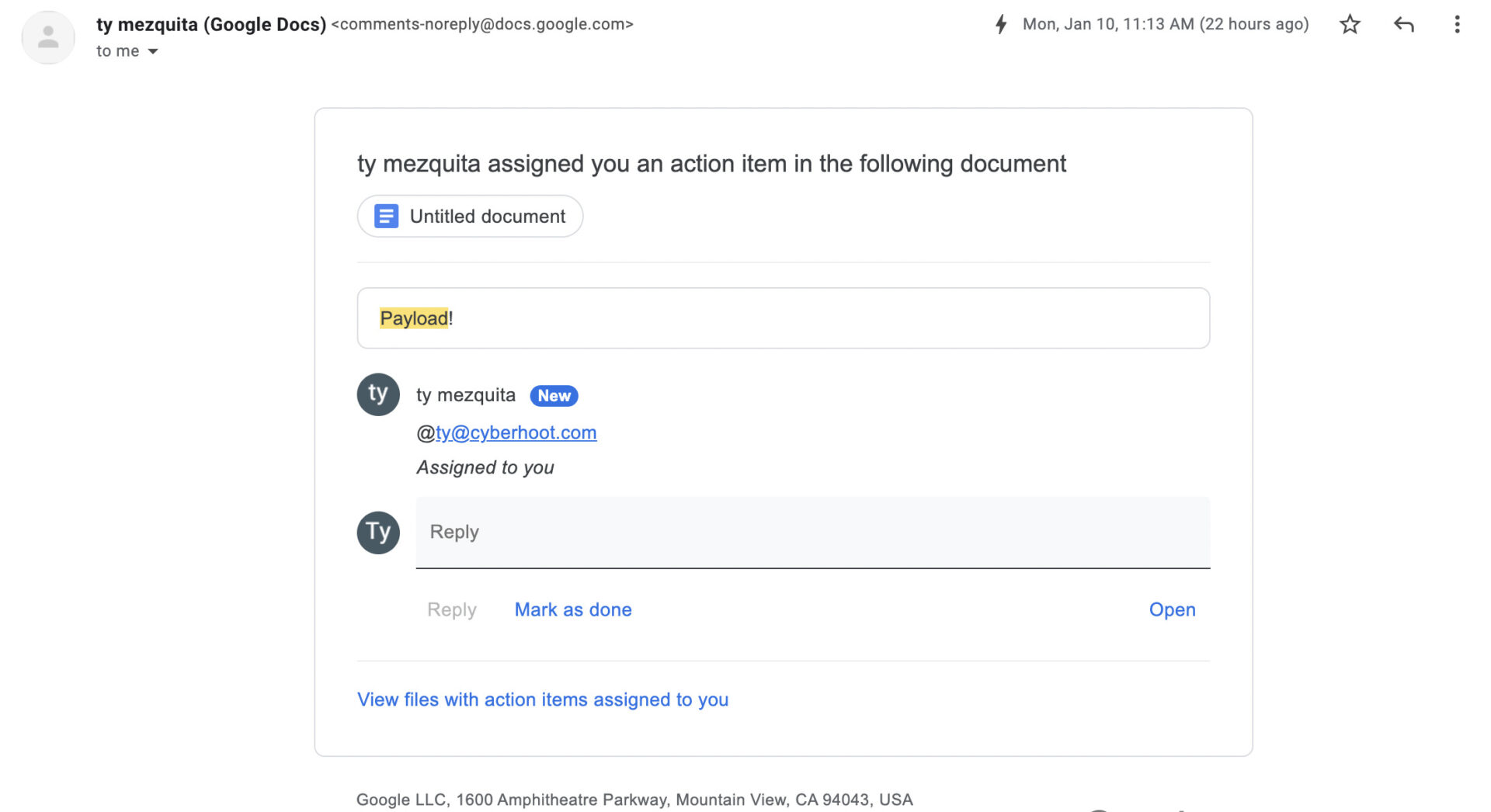
As shown below in the same test email CyberHoot created, It’s difficult to do your proper ‘phishing checklist‘ when receiving these malicious emails; the email address of the sender isn’t shown, just the name of the attacker, which allows bad actors to impersonate legitimate entities to target victims. For example, a hacker can create a free Gmail account, such as [email protected]. They can then create their own Google Doc, comment, and send whatever they like to their intended target.
The malicious intent of the Comment is difficult to catch because the end-user will have no idea whether the comment came from [email protected] or [email protected]. The email will just say ‘Johnny Hacker’ mentioned you in a comment in the following document. If ‘Johnny Hacker’ is a coworker, it will appear legitimate. The email contains the full comment, along with links and text, meaning the victim never has to go to the document, the payload is in the email itself.
All it takes is the attackers setting up a fake Google login landing page, so when the end-user clicks the link, they will be prompted to enter their credentials on the ‘Google’ credential-harvesting site, sending everything to the hackers.
Google Doc “Comments Attack” allows you to spoof anyone, send anything (malicious) to anyone.
What To Do?
CyberHoot recommends that users always cross-reference the email address in the comment to ensure it’s legitimate before clicking on a Google Docs comment. Users can open the Google Document, and hover their mouse over the commenter’s name to see the full email address with their full name.
CyberHoot also recommends that end-users are always following best practices when dealing with potential phishing emails like watching out for:
- Poor spelling or grammar
- Unexpected emails
- Generically addressed emails
- Enticing email attachments
- Urgent actions are needed on your part
- Contains strange-looking links
Additional Cybersecurity Recommendations
Additionally, these recommendations below will help you and your business stay secure with the various threats you may face on a day-to-day basis. All of the suggestions listed below can be gained by hiring CyberHoot’s vCISO Program development services.
- Govern employees with policies and procedures. You need a password policy, an acceptable use policy, an information handling policy, and a written information security program (WISP) at a minimum.
- Train employees on how to spot and avoid phishing attacks. Adopt a Learning Management system like CyberHoot to teach employees the skills they need to be more confident, productive, and secure.
- Test employees with Phishing attacks to practice. CyberHoot’s Phish testing allows businesses to test employees with believable phishing attacks and put those that fail into remedial phish training.
- Deploy critical cybersecurity technology including two-factor authentication on all critical accounts. Enable email SPAM filtering, validate backups, deploy DNS protection, antivirus, and anti-malware on all your endpoints.
- In the modern Work-from-Home era, make sure you’re managing personal devices connecting to your network by validating their security (patching, antivirus, DNS protections, etc) or prohibiting their use entirely.
- If you haven’t had a risk assessment by a 3rd party in the last 2 years, you should have one now. Establishing a risk management framework in your organization is critical to addressing your most egregious risks with your finite time and money.
- Buy Cyber-Insurance to protect you in a catastrophic failure situation. Cyber-Insurance is no different than Car, Fire, Flood, or Life insurance. It’s there when you need it most.
Read More:
Best Antivirus Software in 2024 — Top Antivirus Software Compared