Forecasting and outlining expectations is an inevitable end-of-the-year routine for every industry, more so with digital spheres. Here at StopAd, we’ve already outlined the main trends that will shape the marketing and advertising landscape in 2018, but the picture would be incomplete without considering security aspects, too.
In 2017, the world suffered a record number of data breaches.
In the US alone, there were 1,253 confirmed cases accounting for more than 172.5 million records exposed. Such an overwhelming number of data breaches has made it clear that the problem of online security is not going away anytime soon. Furthermore, it is likely to escalate unless significant checks are put in place to get the situation under control.
It is time to look back on the cybersecurity events of 2017, analyze their long-term effects, outline the lessons we learned (some of them in a really hard way), and explore where things are heading in 2018.
Artificial Intelligence and Machine Learning
If you were alive in 2017, there was no chance of escaping from conversations about artificial intelligence (AI) and machine learning especially, when it comes to making tech predictions and forecasts. The cold truth is that we cannot (and absolutely should not) ignore the possibilities these technologies offer for improving cybersecurity.
Dealing with a variety of threats that differ by scale, attack vectors, and in tactics of execution means that there is an abundance of data, which needs truly rapid analysis.
When it comes to preventing a data breach, every minute counts. Literally.
This is where AI and machine learning come into play, providing the fastest possible way to analyze large volumes of data and detect patterns that would be hard to notice ‘manually.’
Another reason for the advance of AI and machine learning is that these technologies may help proactively detect threat behaviors and build patterns to look out for abnormalities. This includes previously unknown (zero-day) threats that exploit a vulnerability that hasn’t been identified and patched. Once the threat is flagged by AI algorithms and isolated by researchers, there is a higher chance to stop an unfolding attack and minimize its negative consequences, including data breaches.
By removing the workload for analyzing variants of trivial (read: “previously encountered”) threats,
these AI-based monitoring and analysis tools will free up time for cyber-security specialist to address new challenges.
The demand for cyber-security specialists is surging. AI offers a way to amplify human talent rather than replace it.
In 2018, cyber security will definitely continue to expand its AI-based tool inventory. Cybercrooks, in their turn, are also looking for ways to automate their activity, so we will probably see some AI advances in cybercrime as well.
The Internet of Things
The Internet of Things sounded revolutionary when we first heard about it. Today, however, it is a growing market with some of the biggest tech players like Google and Amazon exploiting the technology with great success.
According to Gartner prediction, there will be 21 billion IoT devices in use by 2020, but much like with any other game-changing technology, there are certain risks associated with the IoT.
One of the biggest threats related to this technology is that adversaries may take over connected devices, like routers or IP cameras, and use them for distributed denial of service (DDoS) attacks to paralyze websites or businesses. Of course, it would take hundreds of thousands of devices to implement something like this but, unfortunately, proof of concept already exists.
In fact, Mirai botnet was created exactly for that purpose.
Mirai botnet authors have managed to take over devices and use them to take down a major DNS provider, resulting in the outage of popular sites like Reddit, Twitter, PayPal, and GitHub. The attack worked by scanning the web for IoT devices using the factory preset login and password and then running malicious code on them. Just recently, the man behind the Mirai botnet and his accomplices plead guilty and entered into a plea deal with the government.
There are two factors that make IoT devices a popular target among hackers.
First and foremost, the majority of users simply do not think of the connected devices as computers that can be attacked. Second, as researcher Michael Krebs explains, most vendors fail to communicate a message about the need to secure IoT devices by resetting passwords from default ones.
These two things together result in an escalation of IoT security problem. In 2017 alone, compromised IoT devices contributed greatly to rapid 91% growth of DDoS attacks and the trend is likely to continue gaining momentum.
As usage of connected devices grows both in private households and enterprises, the list of common IoT-related security risks continues to expand. According to predictions by Rapid 7, a leading security research firm, the upcoming year will be marked by the following IoT security risks:
- Malware actors using poorly monitored IoT infrastructure to maintain persistence on the compromised network.
- Abusing public facing IoT devices connectivity to “get a foot in the door” with corporate networks.
- Possible uptick in abuse of hardware (chipsets) vulnerabilities.
- Privacy issues due to attacks on IP cameras, DVRs, and other IoT with cameras that basically turn devices into surveillance tools.
GDPR and Privacy
There is one thing we can be certain of: the privacy discussion is going to be huge in 2018.
The more connected we get, the higher the risks for our personal data. What aggravates the problem even further is that at times we may not even be aware of some risks until we’re faced with dramatic consequences.
Over the last few years, the biggest data privacy concerns have been associated with large companies and data holders failing to keep pace with threat evolution and neglecting implementation of data governance frameworks. Adtech and martech companies collecting user data for analysis and targeting purposes lead to more threats to personal data protection.
This year, the negative effects of poor data management policy resulted in a few catastrophic data breaches.
Because of a record delay in disclosure and awful mitigations, the Equifax case made it to the top of the list. With around 143 million customers affected, there is a high probability that some of the stolen identities may be used for various kinds of mischief, from identity theft to impersonating unknowing persons and even obtaining Extended Validation certificates or trust seals\logos.
Just a few days ago another 1.4 billion login/password credentials surfaced on the dark web—almost two times more entries than in previous password dumps, according to researchers.
In 2018, we expect at least a minor, positive shift in the current situation.
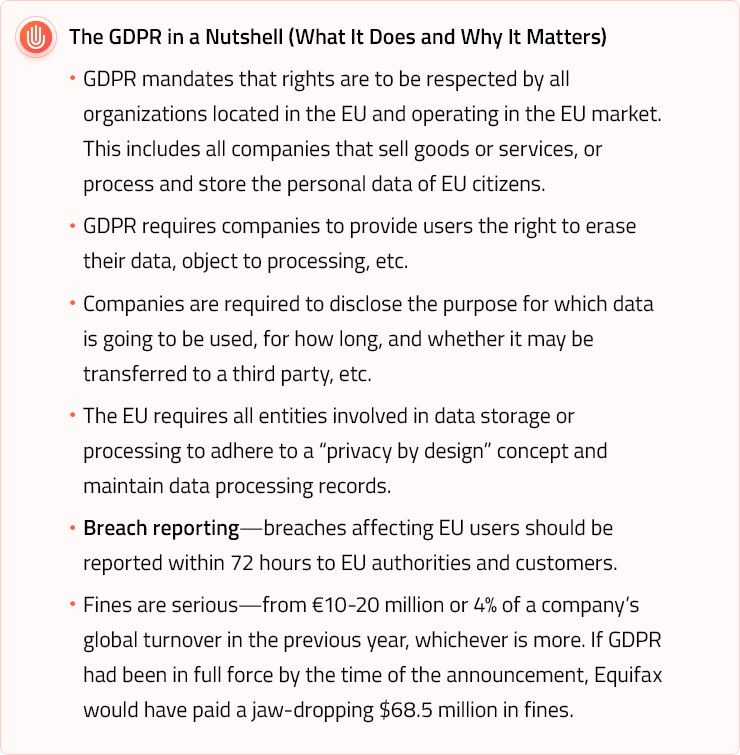
The General Data Protection Regulation (GDPR) and some other data protection legislation will finally come into effect. Of course, it would be naive to believe that data breaches will sink into oblivion with new legislation in place.
Data breaches will most certainly continue in 2018. However, there are grounds to believe that the GDPR enforcement by EU in May 2018 will change the approach to consumer privacy and data processing practices dramatically and not only in the EU.
It is likely that the standards set by the GDPR are going to be used by lawmakers of other countries in the future, thus reshaping the approach to privacy and data protection worldwide. To this day, however, it is still unclear how exactly the EU will enforce GDPR compliance. Meanwhile, 61% of companies haven’t yet started to work on GDPR implementation, which puts them at risk if enforcement procedure will involve rigorous assessment of businesses.
Malvertising
Whether we like it or not, malvertising will most certainly stick around and keep posing online security threats in 2018.
Ads are just another attack vector for hackers. Unfortunately, to all except hackers themselves, malvertising appears to be on the rise.
The number of ads with blacklisted content such as scams, phishing, exploit kits, and malware increased by 18% between the first and the second quarter of 2017, and there is a tendency of annual growth by about 18,65%.
Malvertising is illegal. To spread ads with restricted content, hackers pretend to be legitimate advertisers by registering with ad networks under fake credentials. Once registered, they upload weaponized ads which get distributed to partner websites of these ad networks. When users click on infected ads, they are redirected to fake pages on which their devices are ‘fingerprinted’ and a so-called exploit kit is dropped. This exploit kit then opens a gate for malicious payload delivered from the attackers’ servers.
What makes malvertising extremely fearsome and hard-to-defend-against is that in some cases one doesn’t even have to click on an infected ad to initiate the knock-on effect. If cybercrooks are especially skillful, simply hovering over an ad is enough to get the malicious ball rolling.
Ordinary internet users are not the only target for malvertising criminals.
With much success, malicious ads attack the biggest names in news, including the Huffington Post, Forbes, and The Daily Mail. Speaking of the latter, the British tabloid newspaper is still considered the biggest malvertising target in history. Nearly 156 million monthly visitors (at the moment of attack in 2015) were under threat of a huge hacking campaign. Third-party ads running in the background of the Daily Mail were stealthily redirecting people to exploit kits programed to install malware on their devices.
There are a few reasons why malvertising is becoming increasingly popular with time and will not likely be decisively defeated soon:
- In most of the cases, ad delivery infrastructure is not particularly secure, which makes it an easy task for online criminals to hack an ad server and start distributing weaponized ads across the network of websites.
- The ad industry, browsers, and websites rely heavily on Java and Flash—technologies that are easily and often exploited.
- In many cases, ad platforms and networks neglect the importance of high-quality advertiser verification practices and have no moderation of ads and links.
All this, however, does not mean that malvertising is completely out of control. Simple steps like using an ad blocker, investing in high-quality anti-virus tools, and learning the basics of safe browsing will help you stay away from the majority of malvertising attacks.
Ransomware
In 2017, Ransomware made headlines with large-scale attacks that employed different methods of infection, hitting users and enterprises alike.
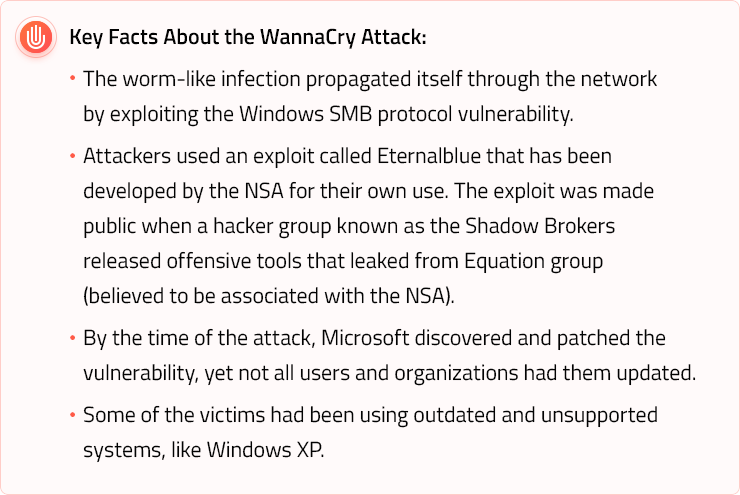
The WannaCry attack, the largest ransomware case of the year, made it clear that apart from causing financial loss and being highly unnerving, cyber attacks are capable of something much worse than that—they can put lives at stake.
When the WannaCry attack happened on May 16, 2017, hospitals in the UK were hit, removing appointments and non-urgent surgeries from the schedule. The attack was a wake-up call showing the world that cyber attacks are no longer only a threat to computers.
A few months later, another ransomware strain known as NotPetya spread like wildfire, hitting mostly Ukrainian users and organizations. Its infection vector was exploiting a compromised update server of a financial software vendor.
The most interesting part about NotPetya is that it was only mimicking ransomware behavior, while its real intention was to disrupt operations and induce data loss. Despite the well-written code to inflict maximum damage, the ransom payment part was clearly lacking some basic sense.
It is predicted that both self-propagating malware and use of ransomware for means other than money (political, cyber-warfare, and alike) will continue in 2018. Furthermore, with the variety of tools that have been published by the Shadow Brokers, other sophisticated attack variants might emerge.
Some experts predict an advance of IoT ransomware that may extort money by stealing sensitive data from devices under threat of spreading it publicly.
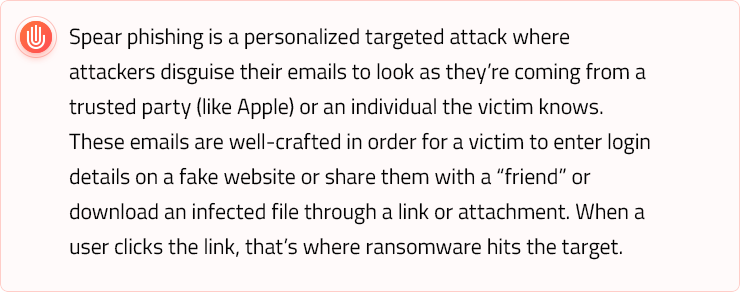
Ransomware will also continue using phishing as the attack vector. In fact, SANS Institute ranked spear phishing emails the second most significant threat with ransomware being at the top.
Lastly, it is projected that ransomware will strengthen its presence through RaaS (ransomware as a service) scheme. This means that individuals with malicious intent can start their own extortion campaign despite having little to no coding skills.
The algorithm is anything but trivial. Knowledgeable criminals develop a ransomware package that requires little to no coding skills to be deployed; low-skilled cybercriminals buy this package and use it for their own attack.
In nearly all the cases, developers of a ransomware package require a one-time payment or a percentage of a revenue generated from an attack where their ransomware package will be used.
The increasing availability of ransomware packages and the fact that little-to-no tech skills are necessary for deployment attacks creates an alarming tendency and calls for new prevention techniques and monitoring processes.
Cryptominers
While Bitcoin is breaking all-time-high records virtually every day, there is another fascinating affair happening on the backstage of cryptocurrency show.
Apart from well-known Bitcoin and Ethereum, there are hundreds of other cryptocurrencies out there, and they pose an indirect sort of threat to virtually any internet user. It might be hard to believe, but you may have nothing to do with cryptocurrencies and still fall victim to the bubble.
How? Fairly simple.
To obtain a certain amount of a cryptocurrency (no matter Bitcoin or any other), it is necessary to solve complicated computational problems. The process is called mining, and it usually requires clusters of video cards to be executed. However, there are certain exceptions.
Monero cryptocurrency, for instance, relies on the power of the computer’s CPU (central processing unit). And this is the point at which the security of ordinary internet users becomes a concern.
Back in September, a tool named “Coinhive” was created. This event marked the beginning of website-based crypto-mining. A .js code installed on a website makes it possible to mine Monero by using visitors’ CPU computational powers, while they spend time on a website. What seems like a smart solution turns out to be another cybercrime affair as, in many cases, users are simply not aware of their CPU unit being used for mining.
There is one more security threat associated with the cryptocurrency boom.
So-called cryptocurrency fever causes malware authors to hijack websites and public Wi-Fi spots (have you heard about the Starbucks case?) Some cases even include attempts to make crypto-hijacking persistent by keeping mining turned on, even when a browser window has been closed, like the case reported by Malwarebytes.
So far, the only way to protect yourself from such a threat is to use adblocker solutions capable of stopping crypto-hijacking scripts.
The Final Word
2017 has finally brought the issue of online security to a head. The record number of data breaches faced this year made it obvious that more efforts should be put in place to prevent the escalation of the problem in the future.
Hopefully, the enforcement of the GDPR and similar data protection regulations will mark the beginning of the new era of online security. But so far, the wisest decision for all internet users would be educating themselves on online security and thinking twice before clicking on a suspicious link or a banner ad.