In a world driven by digital technology, having an online presence is no longer an option for individuals and organizations. However, exposing your business to the digital universe comes with website security risks. That is why constantly monitoring and securing your website applications are paramount to prevent confidential information from being exposed.
In our previous web-based application security series blogs, we covered Open Redirection Vulnerability, Cross-Site Forgery, SQL Injection, Insecure Direct Object Reference (IDOR) and more. In this blog, we will focus on directory traversal attacks and how you can prevent them from occurring.
What is Directory Traversal?
Directory traversal is a web application security vulnerability that allows unauthorized users to access files from different folders or directories that they would otherwise be restricted from accessing. According to Acunetix’s Web Application Vulnerability Report 2019, 46 percent of websites contained high severity vulnerabilities and 87 percent of websites contained medium severity vulnerabilities.
Web servers and web applications store critical information, such as credentials, backups, access tokens and operating system files, that could be easily exposed if vulnerabilities are exploited. There are two levels of defense systems that web servers utilize to protect the data stored – Access Control Lists (ACLs) and the root directory. Website administrators use the Access Control List to authenticate and define the rights granted to certain users or groups. The root directory, on the other hand, is where all the other folders and files reside and is user-restricted. Hackers exploit vulnerabilities in the web server software or flaws in the application using web browsers and guesswork to access arbitrary files.
The Goal Behind Directory Traversal Attacks
According to Positive Technologies, cyberattacks that were carried out to obtain confidential data were a major threat for 68 percent of web applications. With directory traversal attacks, hackers attempt to manipulate web applications to access restricted data from different folders apart from the web root folder. These files are server-internal files that are not accessible to users. A successful attempt can expose critical data, such as path names, file names, credentials and server configuration information, to anonymous hackers. Attackers can also execute malicious commands, alter data, or compromise the entire web server itself.
The Different Names of a Directory Traversal Attack
A directory traversal attack is also commonly referred to as a path traversal, backtracking, or dot dot slash (../) attack because it uses certain special characters. The dot dot slash or “../” tells the browser to move one level back towards the root directory. For instance, the code “x/y/z/../” is equal to “x/y/”, which allows you to find other files from different folders without using the full path.
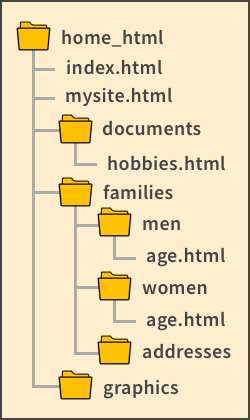
Consider the web directory structure shown below. A relative link can be used from index.html to any folder in the root directory (home_html in this case). To link from hobbies.html to index.html, you must send a request to tell the browser to move up one level from documents to home_html to find the file. The relative link is written as: a href=“../index.html”.
Simplified example of a web directory structure.
How Does a Directory Traversal Attack Work?
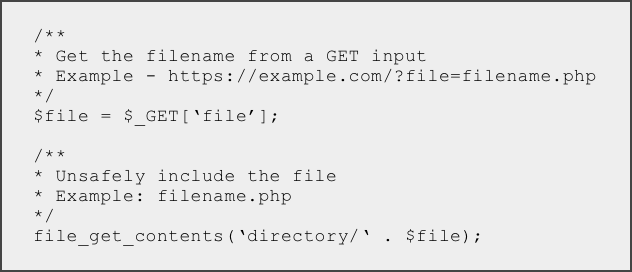
Directory traversal attacks can be easily executed if there are vulnerabilities in the web application code and the web server configuration. Let’s take a look at an example of a PHP code that is susceptible to path traversal attacks.
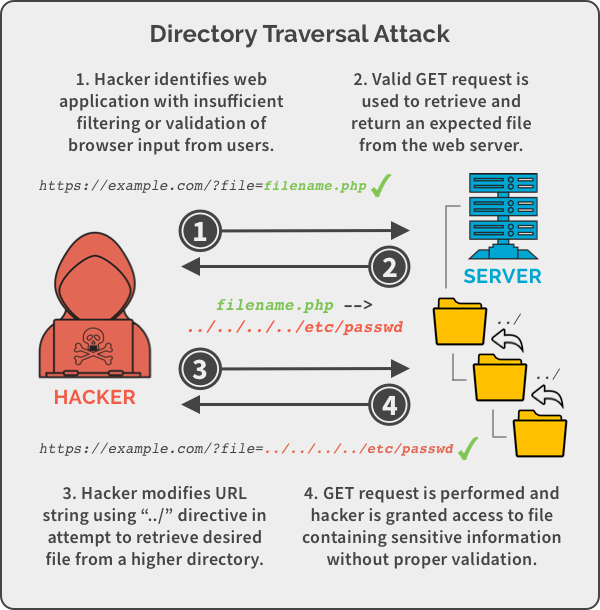
In this case, perpetrators can use the command “http://example.com/?file=../../../../etc/passwd” to manipulate the web application to reveal hidden information of the /etc/passwd system file. Similarly, attackers can exploit path traversal vulnerabilities to access credentials, modify files, or take complete control of the compromised web server.
Simplified example of a Directory Traversal attack.
Detecting Directory Traversal Vulnerabilities
Directory traversal vulnerabilities can be easily detected during the software development process by strongly emphasizing on security. Web vulnerability scanners are highly effective in detecting path traversal vulnerabilities. They trawl the entire website and automatically inspect for vulnerabilities. You can also use code analysis tools, such as Raxis and RIPS Technologies, to analyze and detect faults even before the software is up and running. Once the web application is deployed, penetration testing can be administered to identify any defects. Another method you can use is fuzzing or fuzz testing to experiment with different inputs to check if any of the malformed data causes any problems. Visit OWASP to know more about directory traversal vulnerability testing.
Preventing Directory Traversal Attacks
Directory traversal attacks can be prevented by using the latest web server software and by making sure the server is well maintained and patches are applied. Another important step to take is to make judicious use of the Access Control Lists and ensure appropriate access rights are in place. You can also minimize the risks of such attacks by filtering user-supplied inputs from browsers.
Maintaining Business Continuity in the Event of a Cybersecurity Incident
Although path traversal attacks are among the simpler types of attacks carried out by skilled hackers, they can have a disastrous impact on your business, especially if personal and financial data records are divulged.