- Endpoint security tools are 24% of all IT security spending, and by 2020 global IT security spending will reach $128B according to Morgan Stanley Research.
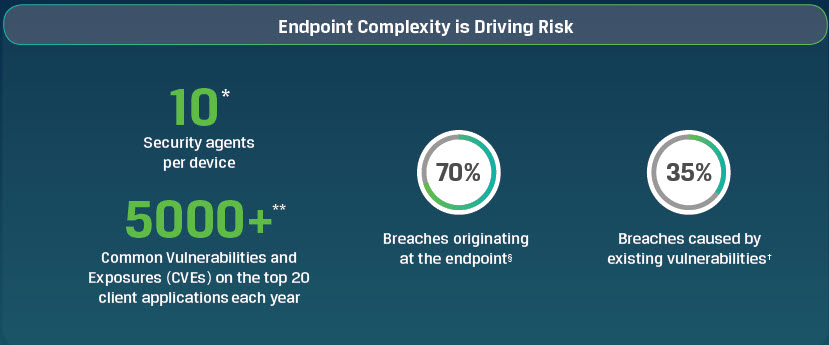
- 70% of all breaches still originate at endpoints, despite the increased IT spending on this threat surface, according to IDC.
To gain a clearer picture of the difficulties organizations face in securing the growing number and variety of endpoints, Absolute released their 2019 Endpoint Security Trends Report. You can access the report here. The insights and conclusions are important for any organization developing and executing a cybersecurity strategy. The research is based on data collected from over 1 billion change events across more than 6 million devices. These devices represent data from 12,000 anonymized organizations in North America and Europe, all using Absolute’s Endpoint Resilience platform. The second phase of the research includes interviews with senior executives from Fortune 500 companies. For more information on the methodology, please refer to page 12 of the study.
Key insights from the report include the following:
- Spending more on endpoint security doesn’t necessarily make an organization safer and can sometimes make it less safe. Organizations are investing more in cybersecurity than before, but they aren’t seeing improvements in safety and security. Gartner’s latest prediction for global spending on information security and risk management is expected to hit $174.5 billion in 2022, with a five-year Compound Annual Growth Rate (CAGR) of 9.2%. Enhancing endpoint controls is a top investment priority leading to increased spending. Over 70% of breaches still happen at endpoints, despite organizations spending millions each year. It’s possible to overspend on endpoint security, which can lower its effectiveness, a key point from the study. IBM Security’s latest Cost of a Data Breach Report 2019 showed that the average cost of a data breach in the U.S. rose from $3.54 million in 2006 to $8.19 million in 2019, a 130% increase over 14 years.
- The more complex and layered the endpoint protection, the greater the risk of a breach. One of the fascinating findings from the study is how the greater the number of agents a given endpoint has, the higher the probability it’s going to be breached. Absolute found that a typical device has ten or more endpoint security agents installed, each conflicting with the other. MITRE’S Cybersecurity research practice found there are on average, ten security agents on each device, and over 5,000 common vulnerabilities and exposures (CVEs) found on the top 20 client applications in 2018 alone. Enterprises are using a diverse array of endpoint agents, including encryption, AV/AM, and Endpoint Detection and Response (EDR). The wide array of endpoint solutions make it nearly impossible to standardize a specific test to ensure security and safety without sacrificing speed. Absolute found organizations are validating their endpoint configurations using live deployments that often break and take valuable time to troubleshoot. The following graphic from the study illustrates how endpoint security is driving risk:
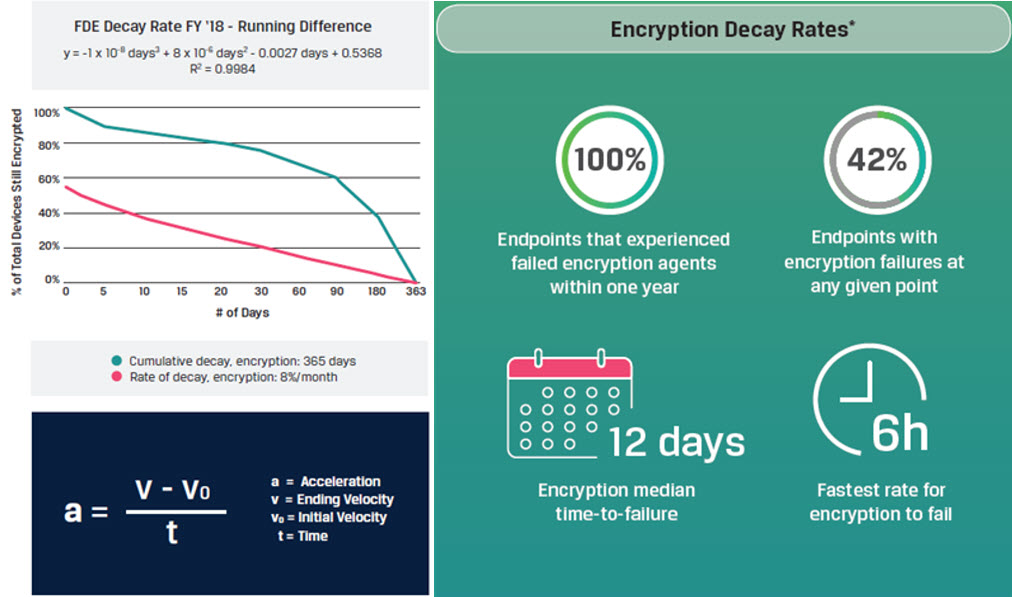
- Endpoint security controls and their associated agents degrade and lose effectiveness over time. Over 42% of endpoints experience encryption failures, leaving entire networks at risk from a breach. They’re most commonly disabled by users, malfunction or have error conditions or have never been installed correctly in the first place. Absolute found that endpoints often failed due to the fragile nature of their encryption agents’ configurations. 2% of encryption agents fail every week, and over half of all encryption failures occurred within two weeks, fueling a constant 8% rate of decay every 30 days. 100% of all devices experiencing encryption failures within one year. Multiple endpoint security solutions conflict with each other and create more opportunities for breaches than avert them:
- One in five endpoint agents will fail every month, jeopardizing the security and safety of IT infrastructure while prolonging security exposures. Absolute found that 19% of endpoints of a typical IT network require at least one client or patch management repair monthly. The patch and client management agents often require repairs as well. 75% of IT teams reported at least two repair events, and 50% reported three or more repair events. Additionally, 5% could be considered inoperable, with 80 or more repair events in the same one-month. Absolute also looked at the impact of families of applications to see how they affected the vulnerability of endpoints and discovered another reason why endpoint security is so difficult to attain with multiple agents. The 20 most common client applications published over 5,000 vulnerabilities in 2018. If every device had only the top ten applications (half), that could result in as many as 55 vulnerabilities per device just from those top ten apps, including browsers, OSs, and publishing tools. The following graphic summarizes the rates of failure for Client/Patch Management Agent Health:
- Activating security at the device level creates a persistent connection to every endpoint in a fleet, enabling greater resilience organization-wide. By having a persistent, unbreakable connection to data and devices, organizations can achieve greater visibility and control over every endpoint. Organizations choosing this approach to endpoint security are unlocking the value of their existing hardware and network investments. Most important, they attain resilience across their networks. When an enterprise network has persistence designed to the device level, there’s a constant, unbreakable connection to data and devices that identifies and thwarts breach attempts in real-time.
Bottom Line: Identifying and thwarting breaches needs to start at the device level by relying on secured, persistent connections that enable endpoints to better detecting vulnerabilities, defending endpoints, and achieve greater resilience overall.