
A study published on August 2 by blockchain analytics company Chainalysis found that there have been 13 different token bridge hacks this year, with the latest being the $190 million Nomad Bridge hack. Their analysis shows that these 13 hacks make up 69% of the total money stolen this year, totaling $2 billion in cryptocurrencies.
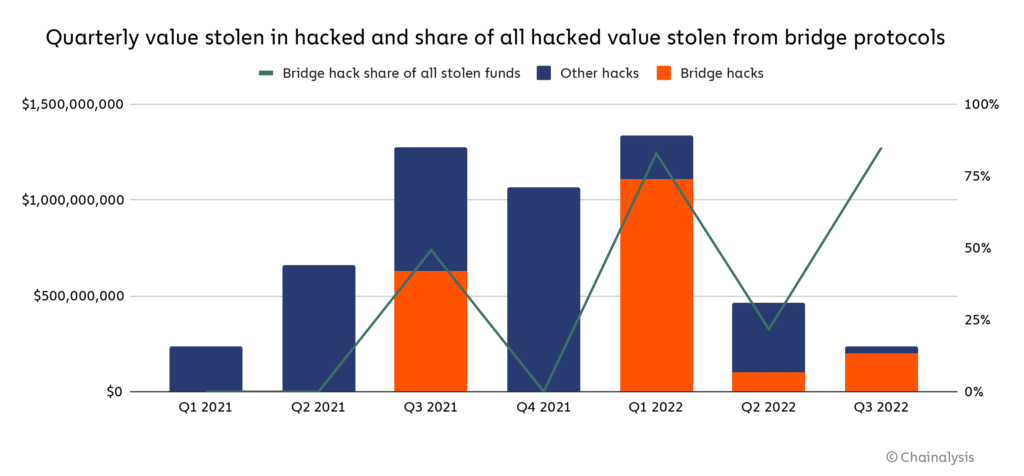
It poses a significant risk to establishing trust in blockchain technology. Cross-chain bridges are more appealing targets for hackers as more money passes through them.
Much more concerning, bridges are currently a top target for North Korean-linked cybercriminals. They have stolen nearly $1 billion in cryptocurrencies so far this year. That’s exclusive via bridges and other DeFi protocols, according to our estimations. In comparison, South Korea’s government-run statistical agency projects that the country will earn $89 million in formal exports in 2020.
However, there is some good news as well.
The astonishing thing is that these services may take precautionary measures to safeguard themselves. For example, in the case of a breach, they may use blockchain technology’s transparency to examine the movement of funds and, hopefully, deter hackers from taking out their ill-gotten profits.
Cross-chain Bridge Protocols
Cross-chain bridges solve the problem of achieving interoperability across multiple blockchains. It is a technology that allows users to transfer assets from one blockchain to another. Although bridge designs vary, customers commonly use cross-chain bridges by moving assets from one asset to the bridge protocol. That’s where the funds are secured into the transaction.
The user is then given an equivalent amount of money in the form of a counterpart asset on the protocol bridges. For example, the Wormhole cross-chain bridge protocol allows users to transfer NFTs and cryptocurrencies between smart contract blockchains such as Ethereum and Solana.
Weakness in a Bridge Causes Crypto Hacks
Bridges are frequently targeted because they provide a centralized source of funds for the ‘bridged’ assets on the receiving blockchain. According to some experts, efficient bridge architecture is still in its early stages. Furthermore, some developers’ awareness of security procedures is still somewhat limited, leaving their systems vulnerable to a hacker attack.
According to a video posted on Twitter on July 22, Nomad CEO James Prestwich believes it will take at least another year or two before there is enough awareness across chain security approaches to establish defenses as a standard. These remarks were made nearly two weeks before the latest incident.
What can the industry do to reduce hacking?
Historically, centralized exchanges were a favorite target for hackers, but advances in security have decreased effective cyber-attacks. The blockchain analytics firm has emphasized the importance of bridges where most cryptocurrency providers invest in security enhancements and training as soon as possible.
Bridges and other cryptocurrency providers must invest in security measures and training. For example, extensive social engineering techniques that rely on people’s tendency to be trusting and negligent when connecting to corporate networks have long been a preferred hacking strategy, particularly among North Korean hackers. Therefore, team members must be trained on these hazards and symptoms.
Related
Battle Infinity - New Metaverse Game
- Listed on PancakeSwap and LBank - battleinfinity.io
- Fantasy Sports Themed Games
- Play to Earn Utility - IBAT Rewards Token
- Powered By Unreal Engine
- Solid Proof Audited, CoinSniper Verified