On February 21, Change Healthcare, which is owned by United Health, was struck by a cyberattack that quickly became one of the most disastrous and costly breaches in cybersecurity history. We got more details about the data breach during the testimony of United Health CEO Andrew Witty, who estimates data of around a third of Americans might have been stolen in that attack.
The attack was carried out by a cybercriminal gang known as AlphV or BlackCat which operates from Russia.
While Witty said in his testimony that the breach affected “a substantial proportion of people in America,” on further probing by lawmakers he said, “I think, maybe a third [of Americans] or somewhere of that level” could be impacted.
He added, “It will take several months before enough information will be available to identify and notify impacted customers and individuals, partly because the files contained in that data were compromised in the attack.”
United Health Acquired Change Healthcare in 2022
United Health acquired Change Healthcare in 2022 for $13 billion after the company successfully defended an antitrust lawsuit by the US Justice Department. Change Healthcare processes nearly half of all medical claims in the US and works with around 5,500 hospitals, 900,000 physicians, 33,000 pharmacies, and 600 laboratories.
The cyberattack severely impacted United Health’s systems and the US healthcare system went into disarray. Healthcare providers were temporarily unable to fill medications and could not get reimbursement for their services from health insurance companies, leading to massive inconveniences for all concerned, including patients.
Following the cyberattack, the US government opened a probe into the data breach which put the data of at least tens of millions of Americans at risk.
Lawmakers Grill United Health CEO Over the Cyberattack
While it’s unusual for lawmakers to be on the same page these days, the coalition grilling Witty was broadly bipartisan. Senate Finance Chair Ron Wyden (D-Ore.) blamed Witty’s leadership (or the lack of it) for the attack.
In his opening remarks, Wyden said, “The failures of CEOs like Mr. Witty, who months in can’t figure out how many people have had their data stolen, validate the FBI’s warning.”
Senator Elizabeth Warren (D-Mass.) termed United Health a “monopoly on steroids” and said it has “bought up every link in the health care chain.” She pointed out that not only is United Health the largest insurer in the country but also the biggest claims processor and the third-largest pharmacy benefit manager.
According to Witty, the hackers “used compromised credentials to remotely access a Change Healthcare Citrix portal.” The fact that the portal did not have multifactor authentication only made their job easier. Since multifactor authentication (MFA) is quite the norm these days for any company that cares about the data credentials of its users, the lack of MFA on the said portal is quite perplexing. The fact that the company, worth nearly half of a trillion dollars, handles the incredibly sensitive data of so many people makes it even worse.
https://twitter.com/2Trump2024/status/1783188816104468907
In his testimony, Witty said, “Change Healthcare was a relatively older company with older technologies, which we had been working to upgrade since the acquisition.”
He added, “But for some reason, which we continue to investigate, this particular server did not have MFA on it.”
Biggest Healthcare Breaches in the US
The United Health data breach would rank among the biggest (or possibly the biggest if a third of the US population is indeed impacted) breaches in the healthcare industry. 2015 was a particularly bad year for healthcare data breaches as 112 million records were either exposed or impermissibly disclosed.
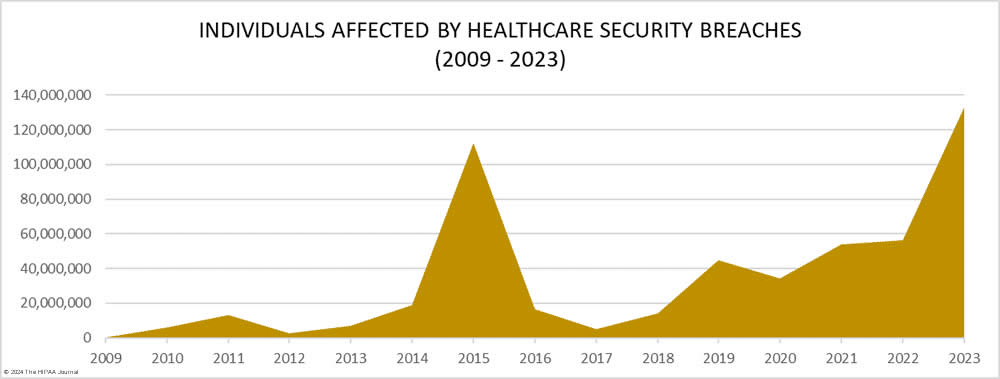
That year, Anthem suffered a massive breach that affected 78.8 million of its members. It was the largest breach until then, and the ePHI of almost 79 million individuals, including names, medical identification numbers, addresses, social security numbers, dates of birth, email addresses, and employment information, were leaked. Anthem eventually paid $16 million to the US Department of Health and Human Services, Office for Civil Rights to settle the violations.
Also breaches at Premera Blue Cross and Excellus affected over 10 million each in 2015. We had a relative lull after 2015 but 2023 set a new record as data of 133 million Americans was breached. By the time we get a full number of United Health data breaches, 2024 could very well be another record year.
In its update on April 22, United Health said, “To date, the company has not seen evidence of exfiltration of materials such as doctors’ charts or full medical histories among the data.”
The company has set up a dedicated website and call center but it said, “Given the ongoing nature and complexity of the data review, the call center will not be able to provide any specifics on individual data impact at this time.”
United Health is still working with third-party partners if data has been published beyond the nearly two dozen screenshots which it said were published by a malicious threat actor on the dark web.
United Health Has Suffered Massive Financial Losses Due to the Breach
UnitedHealth paid a $22 million ransom to BlackCat in the form of Bitcoin – a decision Witty said was his. However, there are other costs associated with the attack, and during the Q1 2024 earnings call, United Health said that during the quarter, it recorded expenses to the tune of $870 million related to the cyberattack. Of these nearly $595 million were direct costs arising from clearinghouse platform restoration and other response efforts.
In the full year, the company expects direct costs associated with the cyberattack to be between $1 billion and $1.15 billion. That doesn’t even include any indirect costs which are certain to become a problem. We also need to account for the damage to the brand and credibility of the United.
All said, the data of millions of Americans is at stake just because United Health did not have the very basic MFA in place.
Piyush Pandey, CEO at Pathlock, said in an emailed statement to Dark Reading, “In this case, MFA could have been an effective gate to the proliferation of this attack. The additional layers of security would make the breach more challenging.”
Also, most users whose data has been breached are yet to be notified. Markets nonetheless have taken note of the breach, and with a YTD loss of nearly 10%, United Health stock is underperforming the markets by a wide margin.
