The rise of remote working due to the COVID-19 pandemic has accelerated the use of Microsoft Teams. The chat-based workspace application is the lynchpin in the Microsoft 365 portfolio. It brings all the other products together and enables team collaboration, and also stores important files, team member details and personal calendars, all from a single interface.
However, the unprecedented adoption of Teams has become a security nightmare for IT professionals. This high-velocity collaboration has translated into bad security practices such as accidental sharing and data leakage.
IT professionals are tasked with the challenge of tightening up the security loopholes in a way that keeps sensitive information secured without compromising on the freedom of users to collaborate — which is the reason for having Teams in the first place.
In this post, we discuss the five Microsoft Teams security best practices that can help keep IT teams and end users vigilant and avoid any data loss, ultimately making the collaboration platform seamless and secure.
Microsoft Teams Security Best Practices
Teams governance policies are the most reliable way to enforce security. These policies determine how the organization will use the app, who can create Teams account(s) and what information folks can share. Appointing a Teams administrator will be crucial in implementing Microsoft Teams security best practices across the entire organization.
Use sensitivity labels
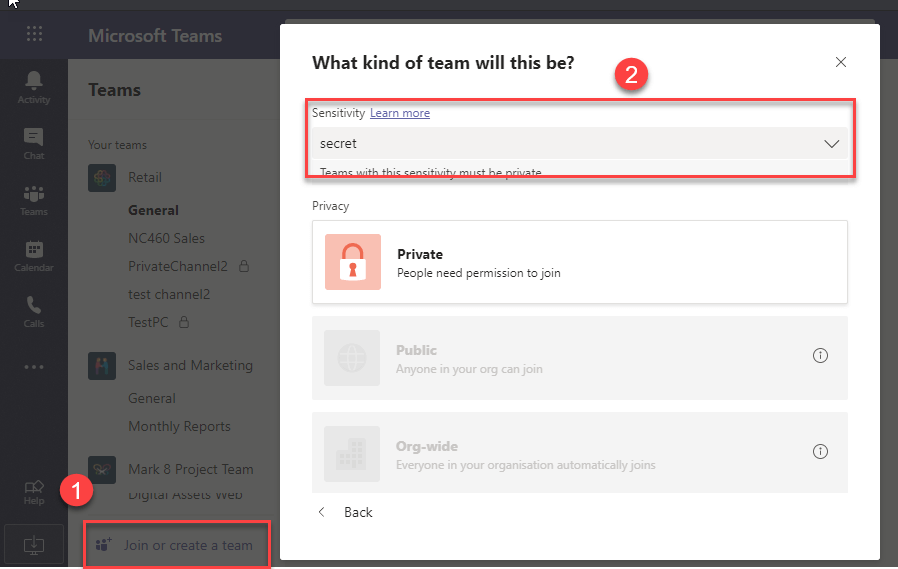
The built-in Microsoft Information Protection (MIP) sensitivity labels let you classify and protect your Teams data without impacting user productivity and collaboration. After a label is applied, the protection settings come into play.
For instance, if you label a Teams Group as “secret,” it gets encrypted. That means people outside your organization can’t access that part of Teams.
Sensitivity labels can help extend your security capabilities in the following ways:
- Enforce protection settings with encryption or watermarks
- Protect content in supported Microsoft 365 apps across multiple platforms and devices
- Protect Teams from third-party apps
Set up DLP
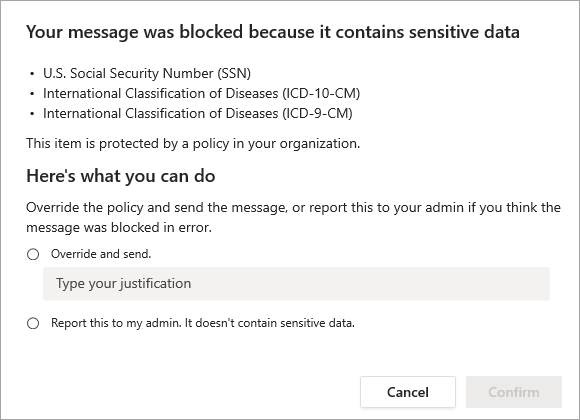
Data loss prevention (DLP) prevents accidental exposure of critical information, which reduces the risk of data breaches. Set up DLP controls based on sensitivity labels, instantly blocking unauthorized users from accessing or sharing data in a Teams channel or a private chat.
In a way, DLP policies help moderate user behavior within Teams. You can even test out these policies before you put them into actual practice. It helps you determine if the policies yield desirable results and helps you fine tune them until you hit the sweet spot.
DLP takes the support of a content analysis engine — files and chats are scanned and any attempt to share sensitive content is blocked. These policies can be applied to guest and external users and works fine on both Teams desktop and web app.
Data access control for Teams
Data access control is a core element when it comes to secure file sharing outside the organization. You can give external access and/or guest access to the Teams channel. These access controls might seem similar, but they are quite different.
External access lets you provide access permission to an entire domain — allowing Teams or Skype users from other domains to call, chat and set up meetings with users inside the organization. It’s like when [email protected] and [email protected] have to work together over Teams without neglecting security.
Guest access lets you provide access permission — allowing an external user to be a member to participate in channels, chats and file sharing. These guests do not need to have a Microsoft 365 account in your organization. Instead, they can use their existing business email accounts.
Here are some ways you can control external and guest access to your Team channels:
1. Prevent “anyone” links with DLP
DLP policy covers conversations with guest access users as well. This ensures you can protect, monitor and control data right within your Microsoft 365 tenant. This way folks won’t get carried away with sharing data carelessly within the Teams ecosystem.
2. Use the Lobby feature
To avoid external users crashing your Teams meetings, use the Lobby feature. External users who try to access your meetings will be redirected to a virtual lobby where they will have to wait for admission. It allows you to vet individuals before they are able to enter the meeting.
3. Enable private channels within a team
Drive focused Teams collaboration among a specific lot of individuals on a need-to-know basis with private channels. All team members, including guests, can be added to a private channel but only channel owners/members have the right to access it.
4. Create security groups
The default settings allow any user with an Exchange Online mailbox to create a team and become a team owner. The simplest way to curb the number of users with this privilege is by creating a Microsoft 365 group. Users in this group will have exclusive permission to create new groups and, by extension, new teams.
5. Configure access settings
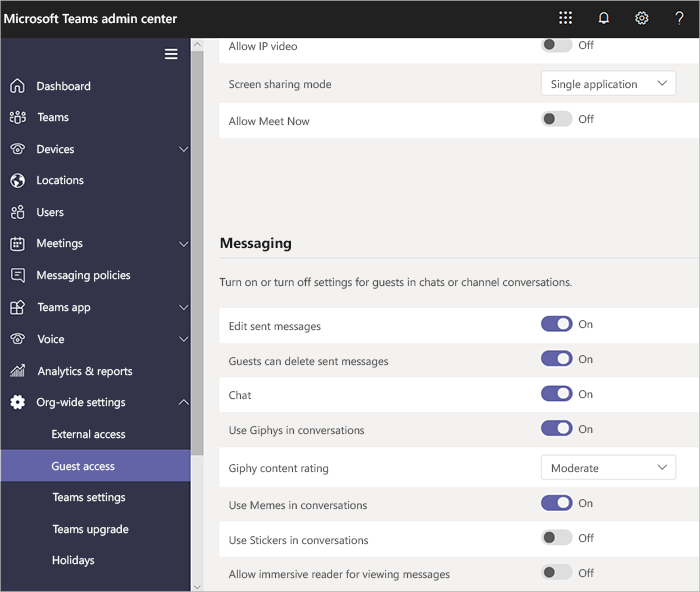
To configure external access settings on Teams admin center, go to Org-wide settings > Select External Access. Admins can allow users to communicate with other Teams or Skype users. You can also set the level of access granted to guest users using the admin center.
Regularly monitor user activity
Monitoring shows how users are adopting and interacting with Teams. Use the insights to understand what set of user behavior to change to achieve better Teams security.
Teams also offer limited monitoring capabilities to avoid blanket permission of third-party apps that require access to user and corporate data. Admins can pre-create an exclusive list of third-party apps that are permitted. In case a team puts in a request for a non-listed app, admins must manually go through the permission policy with a fine comb.
The process might seem cumbersome but it’s better than being compromised. Marriott learned this the hard way when hackers abused a third-party app that the hospitality giant was using for their guest services, resulting in a breach of 5.2 million guest records.
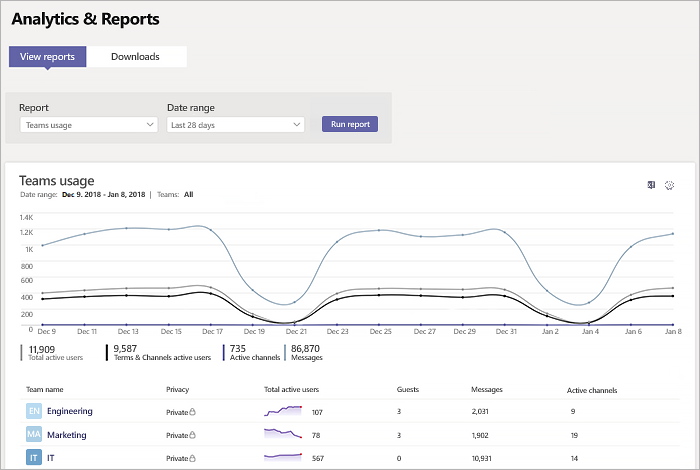
To monitor Teams activity on your admin center, go to Analytics & Reports > View Reports > Usage. You can see various built-in reports and functionality and derive conclusions on user activities, and with the help of technology and education, motivate users to conduct security best practices.
Implement data management policies
Sensitive information stored in Teams presents a security risk, especially if the team has outlived its purpose and the data is just sitting there. Apply these three policies to manage data.
- Retention: Configure Teams retention policies for chat and channel messages and move them to OneDrive and SharePoint once the period is over to free up space in Teams. It ensures built-in compliance while keeping outdated data within the Microsoft 365 ecosystem.
- eDiscovery: A Microsoft 365 tool that lets you identify and return electronic information to be used as evidence in legal cases. With eDiscovery, you can recreate Teams conversations for the legal team to get the entire context of the conversations.
- Expirations: Manage the lifecycle of Office 365 groups by setting an expiration date. Owners of expired groups will be asked to renew their groups. Any group that is not renewed will be temporarily deleted. The group can be restored within 30 days by the group owners or the administrator.