
The global landscape of cybersecurity continues to evolve in 2023 with data breaches becoming more rampant, targeting both individuals and businesses. Contrary to what many might believe, there is a high chance you have been a victim of organized data breaches, perhaps more than once.
According to a report by AAG, an experienced provider of IT support services, on the ‘The Latest 2023 Cyber Crime Statistics,’ threats related to cybersecurity have soared in recent years.
AGG reckons that the situation worsened in the heat of the pandemic as criminals capitalized on misaligned networks brought about by the need for businesses to switch to remote work arrangements.
Astra’s report on ‘160 Cybersecurity Statistics 2023’ projected 33 billion account breaches in 2023 alone, with 8 million cyberattacks recorded so far, considering “on overage, there is a hacker attack every 39 seconds.”
Data Breaches and How To Protect Yourself
With hacker attacks occurring every 39 seconds in 2023, ensuring that you are safe online can no longer be an afterthought, at least according to recent research by the Independent Advisor on company data breaches.
Many companies globally are victims of cyberattacks, phishing scandals as well as ransomware which often culminate in data breaches accompanied by massive payouts and sometimes lawsuits.
A 2022 report on the Cost of Data Breaches by IBM Security painted a grim picture with 83% of all organizations at a global level experiencing at least one breach and leaving 42 million records exposed courtesy of data breaches. This report considered incidences between March 2021 and February 2022.
Such exposed records tend to encompass certain key information including individual identities like first names, email addresses, usernames, passwords, bios, to copies of passports. Some may contain sensitive data on healthcare and financial particulars.
How To Check If Your Data is Safe Online
Despite the rising cases of cybersecurity attacks that end up causing most of the data breaches, resources for individuals to check and verify their safety online are either limited or not easy to find.
However, a recent article by ABC News, authored by Julian Fell, Ben Spraggon, and Matt Liddy pieces together the easiest way to check if your data has been compromised and the action to take.
In the quest to help millions of people online to remain alert and take their data security seriously, the authors turned to a service called ‘Have I Been Pwned? Developed by Troy Hunt, an Australian online security specialist.
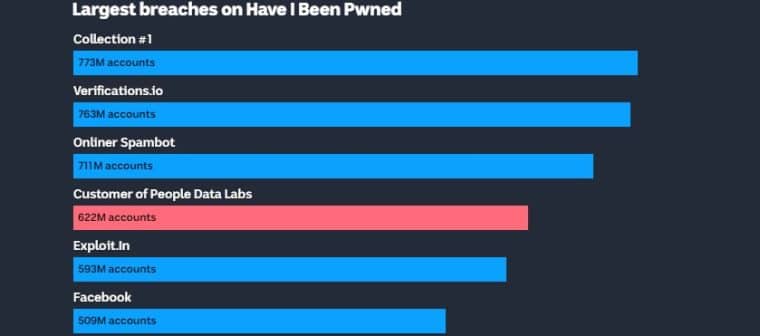
Although complex behind the scenes, Hunt’s platform can track “stolen data across the internet, and is used by numerous national governments, security services, and law enforcement.”
The database gives individuals the opportunity to find out instances when their data was breached.
Similarly, the database will allow you to explore a visual representation of the possible extent of leaked personal information about you on the internet. Additionally, you will learn how a phenomenon called “the mosaic effect” can amplify the dangers we all encounter in the online world.
According to the ABC News article, only your email address is needed to reveal how your leaked data has been used to create a visual representation of your online identity.
How Data Breaches Help Piece Identities Together
ABC News cited Samantha Floreani, a digital rights advocate who gave insights on how repeated data leaks are kneaded together to form an individual’s identity. These identities expose unsuspecting people to cybercrime, fraud, and other incidences of identity theft.
“Maybe you were part of the Optus breach and X, Y, and Z details were leaked,” Floreani said. “Maybe you were also part of another breach that you have no idea about.”
That is what is referred to as the “mosaic effect.” It implies that every individual’s risk compounds with every data leak.
In other words, all information from every breach can be linked to form one single piece of data, which according to the report is your email address.
It is difficult to pin down how these breaches occur, most times an individual will not be aware of some of the companies where their data leaked from until they are exposed.
Over the last few months, I’ve been working on a little project with the ABC here in Australia to help people visualise their exposure in data breaches. This has just gone live today and I reckon they’ve done an amazing job, check it out: https://t.co/K0QXip1Je2
— Troy Hunt (@troyhunt) May 17, 2023
To comprehend how dire the situation is, Floreani and Hunt have also been victims of data breaches, 7 and 28 times respectively.
“I didn’t know why I was there when I found myself in the breach,” Hunt said referring to a breach at Covve, a platform for storing data on contacts in the cloud. He later realized that key information about him had been exposed, including his phone number and email address.
Unfortunately, most companies do not alert users when data breaches occur. Moreover, breaches are only a tiny aspect of the multibillion-dollar market built around data sharing and trading.
“These companies — the data-enrichment industry, data brokers, data intermediaries, and aggregators — turn a profit by compiling data about us from a variety of sources,” Floreani added. “If we were able to see the full extent of all the pieces of information available about me, you’d probably end up with a high-definition mosaic portrait.”
When data breaches occur, the information can be used in various ways including targeted advertising as well as criminal activity. These breaches may take place on social media platforms like Twitter, Facebook, and other companies that collect data.

It is up to you to ensure that your data stays safe and does not land in the hands of hackers and other criminals.
There are numerous VPN privacy tools people can use to ensure they are safe and their data is secure, some with the ability to significantly reduce the mosaic effect. However, Floreani believes regulations should be in place to ensure data is safe to protect the integrity of the internet as a resource.
“We need robust regulation to protect our privacy, challenge the data-extractive business models of digital platforms,” she said.
Related Articles:
- The Best Cheap VPN in 2023 | Top VPNs for Less Than $2 per Month
- Intel Announces 1 Trillion Parameter ChatGPT Competitor Aurora genAI
- Lack of Regular App Updates Is Holding Back 62% of Mobile Development Companies
What's the Best Crypto to Buy Now?
- B2C Listed the Top Rated Cryptocurrencies for 2023
- Get Early Access to Presales & Private Sales
- KYC Verified & Audited, Public Teams
- Most Voted for Tokens on CoinSniper
- Upcoming Listings on Exchanges, NFT Drops