When Democratic National Committee (DNC) Chief John Podesta’s aide forwarded him an email that claimed Podesta’s Gmail account was hacked, Podesta did what most of us would have done: He clicked the link within the email and was directed to a website where he was prompted to enter a new password. He did so and then went about his daily business. Unfortunately for Podesta, the Democratic Party, and Hillary Clinton’s presidential campaign, the email sent to Podesta wasn’t from Google. Rather, it was a spear-phish attack from a Russian hacking group named “Fancy Bear.”
Even if you’ve never heard of the term “spear-phishing,” you’ve undoubtedly heard of these kinds of attacks. You’ve probably even been a target of them. These attacks typically take the form of customer support emails that ask you to change credentials or they can be sent via fake email addresses to businesses asking for highly personal customer or employee data. For example, in 2015, employees of Ubiquiti Networks transferred $46.7 million to overseas accounts at the behest of emails the employees assumed were sent by Ubiquiti executives. In reality, hackers created spoof email accounts that bore a resemblance to actual Ubiquiti executive accounts and tricked the employees.
Based on data from a recent study conducted by email security company IronScales, 77 percent of attacks are laser-focused, targeting 10 accounts or fewer, with a third of attacks targeting only one account. Attacks are short, with 47 percent lasting less than 24 hours, and 65 percent lasting fewer than 30 days. Traditional spam filters and endpoint protection tools aren’t catching the attacks. For every five attacks identified by spam filters, 20 attacks made it into a user’s inbox.

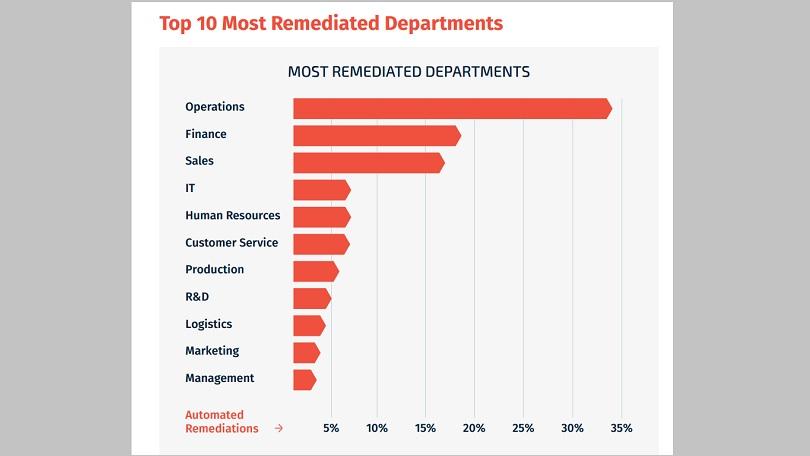
(Image Via: IronScales)
“We see attackers spending much more time studying their targets than in years past, running a very comprehensive reconnaissance process,” said Eyal Benishti, CEO of IronScales. “As a result, phishing emails have become highly targeted and tailored to the target company, as attackers are able to gather information through reconnaissance that helps them craft emails to look like legitimate internal communication. For example, we’ve seen some attacks use the organizations’ lingo and signatures, and the content is very much in context to what is currently running inside the company and between trusted parties.”
Jeff Pollard, Principal Analyst at Forrester Research, added that these attacks are also growing in sophistication. “Attacks are getting more sophisticated both in terms of the lures used to get people to click and in terms of the malware used to gain entry to systems,” said Pollard. “But that is what we expect given that cybersecurity is a constant battle between defenders and attackers.”
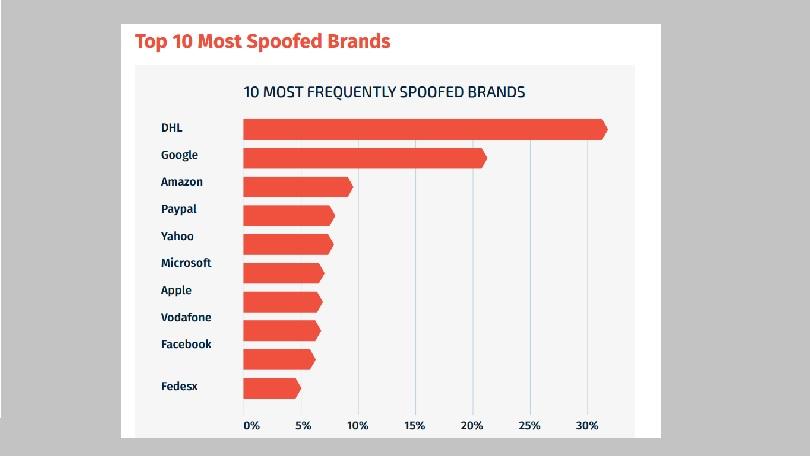
(Image Via: IronScales)
The Solution
To combat these attacks, companies are turning to anti-phishing software to detect and flag incoming attacks. Anti-spam and anti-malware tools are no-brainers for any company hoping to protect business data. But companies such as IronScales are taking it a step further by layering in machine learning (ML) tools to proactively scan for and flag sketchy phishing emails. Additionally, because ML lets the tools compile or remember scam data, the software learns and improves with every scan.
“The technology makes it harder on the attacker to fool the defender with small tweaks that normally bypass a signature-based solution,” said Benishti. “With ML, we can quickly cluster different variants of the same attack and more effectively fight against phishing. In fact, from our analysis, ML is the best way to train a system to tell the difference between legitimate emails coming from a trusted partner or colleague versus a non-legitimate one.”
Technology isn’t the only safeguard against these forms of attacks. Education and caution are perhaps the most important defenses against spear-phishing attacks. “Some businesses are aware of the threats, though others mistakenly believe that their current solution is protecting against targeted attacks,” said Benishti. “It’s very important to understand that using the same defense mechanisms and expecting different results in future attacks simply won’t do. Using technology alone against advanced attacks, which put people as targets, will always fail, as will relying solely on employee awareness and training…People and machines working closely together to close this gap of unknown attacks is the only way to reduce risk.”
(Image Via: IronScales)
How to Stay Safe
Here are a few very simple ways to ensure that you and your company don’t get scammed:
- Make sure company emails are labeled “INTERNAL” or “EXTERNAL” in the subject line.
- Verify suspicious or risky requests by phone. For example, if your CEO emails you and asks you to send someone’s personal health data, then give him or her a call or send a chat message to verify the request.
- If a company asks you to change your password, then don’t use the link in the email notification; go directly to the company’s website instead and change your password from there.
- Never, under any circumstances, should you send your password, social security number, or credit card information to someone in the body of an email.
- Don’t click on links in emails that contain no other text or information.
“As defenses improve, so do attacks,” said Pollard. “I think we’ll see more targeted spear-phishing and whaling campaigns. We’ll also see a rise in social media phishing and scamming, which is an area that isn’t as mature from a security standpoint as email security is.”
Unfortunately, no matter how careful you may be, attacks will intensify and become more intelligent. You can do everything in your power to educate yourself and your employees, you can build out an anti-phishing defense backed by new technologies, and you can take every precaution possible. But, as Pollard noted, “it only takes one bad day, one misclick, or one rushed user trying to clean out an inbox, to lead to catastrophe.”